
- My presentations

Auth with social network:
Download presentation
We think you have liked this presentation. If you wish to download it, please recommend it to your friends in any social system. Share buttons are a little bit lower. Thank you!
Presentation is loading. Please wait.
Intro to Web Application Security
Published by Kimberly Gray Modified over 6 years ago
Similar presentations
Presentation on theme: "Intro to Web Application Security"— Presentation transcript:

Nick Feamster CS 6262 Spring 2009
What is code injection? Code injection is the exploitation of a computer bug that is caused by processing invalid data. Code injection can be used by.
Copyright © The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the OWASP License. The OWASP.
OWASP Web Vulnerabilities and Auditing

SEC835 OWASP Top Ten Project.

The OWASP Foundation OWASP Top Kuai Hinojosa Software Security Consultant at Cigital OWASP Global Education Committee OWASP.

Creating Stronger, Safer, Web Facing Code JPL IT Security Mary Rivera June 17, 2011.

Security Issues and Challenges in Cloud Computing

Chapter 9 Web Applications. Web Applications are public and available to the entire world. Easy access to the application means also easy access for malicious.

Information Networking Security and Assurance Lab National Chung Cheng University The Ten Most Critical Web Application Security Vulnerabilities Ryan J.W.

It’s always better live. MSDN Events Securing Web Applications Part 1 of 2 Understanding Threats and Attacks.
Information Networking Security and Assurance Lab National Chung Cheng University 1 Top Vulnerabilities in Web Applications (I) Unvalidated Input: Information.

Injection Attacks by Example SQL Injection and XSS Adam Forsythe Thomas Hollingsworth.

Web Application Vulnerabilities Checklist. EC-Council Parameter Checklist URL request URL encoding Query string Header Cookie Form field
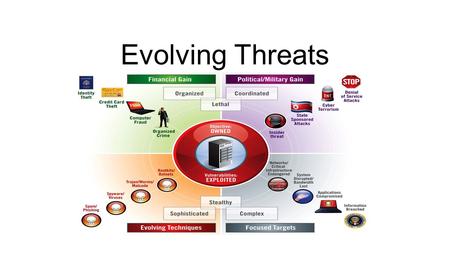
Evolving Threats. Application Security - Understanding the Problem DesktopTransportNetworkWeb Applications Antivirus Protection Encryption (SSL) Firewalls.

OWASP Zed Attack Proxy Project Lead
Cosc 4765 Server side Web security. Web security issues From Cenzic Vulnerability report

CSCD 303 Essential Computer Security Winter 2014 Lecture 12 – XSS, SQL Injection and CRSF Reading: See links - End of Slides.

Lets Make our Web Applications Secure. Dipankar Sinha Project Manager Infrastructure and Hosting.
About project
© 2024 SlidePlayer.com Inc. All rights reserved.
- Preferences

Web Security - PowerPoint PPT Presentation


Web Security
An introduction. web engineering – powerpoint ppt presentation.
- Faran Sabir
- BS-IT-14-M-1009
- 1.Introduction
- 2. Security threats
- 3. Best Practices Recommendation
- 4. Security standards
- 5. Security technology
- Web application security is a branch of Information Security that deals specifically with security of websites, web applications and we b services.
- At a high level, Web application security draws on the principles of application security but applies them specifically to Internet and Web systems.
- With the emergence of Web, increased information sharing through social networking and increasing business adoption of the Web as a means of doing business and delivering service, websites are often attacked directly.
- Hackers either seek to compromise the corporate network or the end-users accessing the website by subjecting them to drive-by downloading.
- Industry is paying increased attention to the security of the web applications themselves in addition to the security of the underlying computer network and operating systems.
- The majority of web application attacks occur through cross-site scripting (XSS) and SQL injection attacks which typically result from flawed coding, and failure to sanitize input to and output from the web application.
- Phishing is another common threat to the Web application and global losses from this type of attack in 2012 were estimated at 1.5 billion.
- Secure web application development should be enhanced by applying security checkpoints and techniques at early stages of development as well as throughout the software development lifecycle.
- Special emphasis should be applied to the coding phase of development.
- OWASP is the emerging standards body for Web application security. In particular they have published the OWASP Top 10 which describes in detail the major threats against web applications.
- The Web Application Security Consortium (WASC) has created the Web Hacking Incident Database and also produced open source best practice documents on Web application security.
- While security is fundamentally based on people and processes, there are a number of technical solutions to consider when designing, building and testing secure web applications.
- At a high level, these solutions include
- Web application security scanner
- Web application firewalls (WAF)
- Password cracking
- Black Box testing tools such as Web application security scanners, vulnerability scanners and penetration testing software.
- White Box testing tools such as static source code analyzers.
- Fuzzing Tools used for input testing.
- Vulnerability Scanner
- It is used to provide firewall-type protection at the web application layer.
- Password Cracking tools for testing password strength and implementation.
- https//en.wikipedia.org/wiki/Web_application_secu rity
- https//en.wikipedia.org/wiki/OWASP
PowerShow.com is a leading presentation sharing website. It has millions of presentations already uploaded and available with 1,000s more being uploaded by its users every day. Whatever your area of interest, here you’ll be able to find and view presentations you’ll love and possibly download. And, best of all, it is completely free and easy to use.
You might even have a presentation you’d like to share with others. If so, just upload it to PowerShow.com. We’ll convert it to an HTML5 slideshow that includes all the media types you’ve already added: audio, video, music, pictures, animations and transition effects. Then you can share it with your target audience as well as PowerShow.com’s millions of monthly visitors. And, again, it’s all free.
About the Developers
PowerShow.com is brought to you by CrystalGraphics , the award-winning developer and market-leading publisher of rich-media enhancement products for presentations. Our product offerings include millions of PowerPoint templates, diagrams, animated 3D characters and more.

Web Application Security training
Jul 19, 2014
600 likes | 697 Views
Web Application Security training. Agenda. Introduction OWASP: a quick review Common vulnerabilities and solutions (Hacking demos) Best practices. Agenda. Introduction OWASP: a quick review Common vulnerabilities and solutions (Hacking demos) Best practices. Introduction.
Share Presentation
- source code
- hacker web server storage
- common vulnerabilitiesa8
- insecure direct object references
- common vulnerabilities

Presentation Transcript
Agenda • Introduction • OWASP: a quick review • Common vulnerabilities and solutions (Hacking demos) • Best practices
Introduction • Whatis application security? • Definition : "Information security is a process to protect data against unauthorized access, use, dissemination, destruction or modification. “ (Wikipedia)
Introduction Extended definition: Software Part integrated in Information Systems that manage:● The information security● The integrity of I.S.● Confidentiality of IS..
Introduction What is at stake?● S.I. = business core ● S.I. = data set (sensitive data) Consequences if:● Data Theft (sale to a competitor)● Data Violation (deletion / modification)● Degradation of services
Introduction • Web application source code, independent of languages and platforms, is a major source for vulnerabilities.
OWASP(1/2) • What is OWASP? • OWASP= Open Web Application Security Project • A standard for performing application-level security verifications. • A Guide : document provides detailed guidance on web application security
OWASP(2/2)TOP 10
Agenda • Introduction • PCI DSS : a quick review for developers • Common vulnerabilities and solutions (Hacking demos) • Best practices
Common vulnerabilitiesOWASP TOP 10
Common vulnerabilitiesA1 : Injection
Common vulnerabilitiesA1 : SQL Injection (login bypass example) POST http://www.mysite.com/login.asp HTTP/1.1 login=admin&pwd=' or 1=1-- POST http://www.mysite.com/login.asp HTTP/1.1 login=admin&pwd=Ultra-s3cur3-p@ssw0rd! 1 select * fromuserswherelogin ='admin'AND password='' or 1=1--' select * fromuserswherelogin ='admin'AND password='Ultra-s3cur3-p@ssw0rd!' 3 HTTP Request SQL Query ID | LOGIN | ROLE1 | admin | superuser SQL Answer 4 Firewall Firewall Workstation / Browser Web Server Web App Web App Database Server 80 / 443 Web App Web App HTTP Response <html> <%if (sqlResults.isEmpty()){%> <h1>Access Denied</h1> <%}else{%> <h1>Hello user<%=login%></h1> <%}%> </html> 6 HTTP/1.x 200 OK Content-Type: text/html Content-Length: 2000 <html> <h1>Hello user admin</h1> </html> Http Request Parsing 2 5 Server page
Demo : Sql injection Common vulnerabilitiesA1 : SQL Injection (demos)
Solution (2/2) Common vulnerabilitiesA1 : Injection
Demo :Solution Common vulnerabilitiesA1 : Injection
Common vulnerabilitiesA2 : Cross-Site Scripting (XSS)
Common vulnerabilitiesA2 : Cross-Site Scripting (identity theft example) • /editObject.asp?id=100&newTitle=<javascript>alert(document.cookie)</script> Database Server Web Server /showObject.asp?id=100 Hacker Web Server Storage <html><body> <h1>Article 100</h1> <javascript> alert(document.cookie) </script> </body></html> /cookie.cgi?SESSIONID=002E42EF3CBRA29F3
Demo : XSS Attack Common vulnerabilities A2 : XSS(demos)
Demo : Solution Common vulnerabilities A2 : XSS(demos)
Common vulnerabilitiesA3 :Broken Authentication and Session management
Demo Common vulnerabilitiesA3 :Broken Authentication and Session management
Common vulnerabilitiesA4 : Insecure Direct Object References
Common vulnerabilitiesA4 : Insecure Direct Object References • Parameter tampering : authorization bypass example /listMyAccounts.asp /account.asp?id=12 /account.asp?id=15 Database Server Web Server "select * from account where owner="+session(userid) select * from account where id=15 ID | ACCOUNT | BALANCE 15 | bill gates| 999 999 999 € ID | ACCOUNT | BALANCE 12 | check| 1 000 € 30 |saving| 20 000 € <html><body> <h1>List of accounts</h1> <a href=/account.asp?id=12>Check</a> <a href=/account.asp?id=30>Saving</a> </body></html> <html><body> <h1>Bill gates private account</h1> […] </body></html>
Demo Common vulnerabilitiesA4 : Insecure Direct Object References
Common vulnerabilitiesA5 : Cross Site Request Forgery (CSRF)
Common vulnerabilitiesA5 : Cross Site Request Forgery (CSRF) When the customer read this news An authenticated connection is done to his bank web site https://bank.com/transfert.asp?Montant=2500&compteDestination=25302252232552 One fraudulent transfert have been proceed (du to the CSRF vulnerability) bank.com Blog.net • Hackers have create a malicious news on Blog.net • It contains the following link • <imgsrc=“https://bank.com/transfert.asp?Montant=2500&compteDestination=25302252232552 ”> A customer is connected to his bank web site and To another (already hacked) web site (blog.net)
Demo Common vulnerabilitiesA5 : Cross Site Request Forgery (CSRF)
Demo • Solution Common vulnerabilitiesA5 : Cross Site Request Forgery (CSRF)
Common vulnerabilitiesA6 – Security Misconfiguration
Common vulnerabilitiesA6 – Security Misconfiguration (ex)
Demo • Access to jsp pages Common vulnerabilitiesA6 – Security Misconfiguration (ex)
Common vulnerabilitiesA7 – Failure to Restrict URL Access
Common vulnerabilitiesA7 – Failure to Restrict URL Access • Attacker notices the URL indicates his role /user/getAccounts • He modifies it to another directory (role) /admin/getAccounts, or /manager/getAccounts • Attacker views more accounts than just their own
Common vulnerabilitiesA8 – Insecure Cryptographic Storage
Finance Transactions Accounts Administration Communication Knowledge Mgmt E-Commerce Bus. Functions Custom Code Common vulnerabilitiesA8 – Insecure Cryptographic Storage Victim enters credit card number in form 1 Log files Malicious insider steals 4 million credit card numbers 4 2 Error handler logs CC details because merchant gateway is unavailable 3 Logs are accessible to all members of IT staff for debugging purposes
Demo • Solution Common vulnerabilitiesA8 – Insecure Cryptographic Storage
Common vulnerabilitiesA9 – Insufficient Transport Layer Protection
Common vulnerabilitiesA9 – Insufficient Transport Layer Protection illustration External Victim Backend Systems Custom Code Employees 2 1 External attacker steals credentials and data off network Internal attacker steals credentials and data from internal network External Attacker Internal Attacker
Common vulnerabilitiesA10 – Unvalidated Redirects and Forwards
Best practicesSecurity principles (1/10) INPUT IS EVIL • It’s better to consider that users or external systems that communicate with your application may be someday harmful for your application • E.g.: • A user that tries to input unexpected data in a form • A partner’s system, with privileged access to one of your applications, that is compromised by a hacker or worm and tries to attack your network VALIDATE, VALIDATE, VALIDATE !!!
- More by User

Web Application Security
Web Application Security. Chris Edwards Quintin Cutts Steve McIntosh. http://xkcd.com/327/. SQL Injection . Example: Look up customer details, one at a time, via customer ID. $ mysqli = new mysqli ($host,$ dbuser ,$ dbpass , $ dbname ); $id= $_POST{'id'};
702 views • 41 slides

Web Application Security. Presented by Jay Jaeger and Kevin Acker. Overview. Application vulnerabilities are serious: your data and infrastructure are at risk.
457 views • 24 slides

Presented at: Nextbridge LHR C1 June 6, 2012. Web Application Security. Best Programming Practices. Topics we covered in previous session. What is Information What is Information Security What is Risk Corporate Security How we are linked with Corporate Security
506 views • 26 slides

Web Application Security. There are three main security concerns your web apps need to address. Impersonation A client pretends to be someone else in order to gain access to your site Your site needs to authenticate clients to prevent this Upgrading
301 views • 16 slides

Spring 2014. CS 155. Web Application Security. John Mitchell. Reported Web Vulnerabilities "In the Wild". Data from aggregator and validator of NVD-reported vulnerabilities. Three top web site vulnerabilites. SQL Injection Browser sends malicious input to server
1.23k views • 90 slides
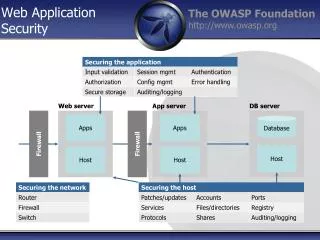
Web Application Security. Web server. App server. DB server. Firewall. Firewall. A pps. A pps. Database. Host. H ost. H ost. Web Application B ehaviour. HTTP is stateless and hence requests and responses to communicate between browser and server have no memory.
304 views • 14 slides
CS 361S. Web Application Security. Vitaly Shmatikov (most slides from the Stanford Web security group). Reading Assignment. “Robust Defenses for Cross-Site Request Forgery” “Advanced SQL Injection” “Cross Site Scripting Explained” “Postcards from the Post-XSS World”. Web Applications.
2.14k views • 112 slides

Lecture on. Web Application Security. How to build secure e-business applications. Walter Kriha. To understand Web application security, you have to understand Web applications. To understand Web applications, you have to understand how to design and build them.
524 views • 32 slides

Web Application Security. Vulnerabilities, attacks, and countermeasures. Who Am I?. Marco Cova ( [email protected] ) PhD candidate UCSB Computer Science Dept. Computer Security Group Research focus Vulnerability analysis of web applications
917 views • 72 slides

Web Application Security. There are three main security concerns your web apps need to address. Impersonation A client pretends to be someone else in order to gain access to your site Upgrading A client gains access to restricted aspects of your web app Eavesdropping
256 views • 16 slides

Web Application Security. (and why it matters to YOU!) By Mark Bristow and Doug Wilson. Your presenters today. Doug Wilson Security Lead and Network/Systems Engineer for EMIB at NIH [email protected] Mark Bristow Application Security Engineer at GAO
434 views • 30 slides

Web Application Security. An Introduction. OWASP Top Ten Exploits. *Unvalidated Input Broken Access Control Broken Authentication and Session Management *Cross Site Scripting (XSS) Flaws Buffer Overflows *Injection Flaws *Improper Error Handling *Insecure Storage *Denial of Service
648 views • 19 slides

Web application security
Web application security. Sebastian Lopienski & Marthe Engebretsen CERN Computer Security Team HEPiX Autumn 2009, LBL See also: http://indico.cern.ch/contributionDisplay.py?contribId=38&sessionId=13&confId=27391. Outline. Why Web applications Threats Web at CERN Possible solutions Tools
586 views • 28 slides

Web Application Security. UTO Information Security Office Aug 25, 2010. Rev 1. Overall recommendations. Under the direction of the Information Security Office: Resolve lack of secure socket layer logins and missing digital security certificates on asu.edu academic and administrative sites
179 views • 5 slides
Suma Soft’s Web Application Security solutions define threat and vulnerabilities. We offer a secured network infrastructure that consists of routers, firewalls, and switches. Web application security analyzes all user access to your business-critical web applications and protects your applications and their data from attacks. Get a risk free trial>>https://goo.gl/W8BD8h
151 views • 6 slides

Web Application Security. Authentication and Authorization in IIS6 and ASP.NET. Outline. IIS 6 process model ASP.NET security contexts The HTTP pipeline Authentication Authorization Forms Authentication. IIS 6. IIS is not installed by default
403 views • 36 slides

Web Application Security. Reading. Required: Stuttard and Pinto: Chapter 3 Recommended: Csilla Farkas, Michael N. Huhns: Securing Enterprise Applications: Service-Oriented Security (SOS). CEC/EEE 2008: 428-431. http://www.cse.sc.edu/~farkas/publications/SOS-cec.pdf. Key Problem Factors.
384 views • 34 slides

Web Application Security. Introduction. Security is a process of authenticating users and controlling what a user can see or do. Server. Web. DB Server. 3-tier architecture. Web Browser. Some Internet Security Protocols. Application Layer Security Electronic mail security
273 views • 21 slides

Web Application Security. James Walden Northern Kentucky University [email protected]. Is your web site secure?. Is your web site secure?. Is your web site secure?. Yes, we deployed SSL, firewall, etc. Does SSL protect all communications? What about stored data?
420 views • 36 slides

IMAGES
VIDEO