JavaScript seems to be disabled in your browser. For the best experience on our site, be sure to turn on Javascript in your browser.
Newly Launched - AI Presentation Maker

AI PPT Maker
Powerpoint Templates
PPT Bundles
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Cyber Security
Business PPT
Digital Marketing
Digital Transformation
Human Resources
Product Management
Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories

Top 10 App Security PowerPoint Presentation Templates in 2024
Introducing our comprehensive App Security PowerPoint presentation, designed to empower organizations with the knowledge and strategies needed to safeguard their applications against evolving cyber threats. This fully editable and customizable template provides a structured approach to understanding the critical aspects of app security, including threat modeling, secure coding practices, and vulnerability assessments. With visually engaging slides, you can easily communicate complex concepts, making it ideal for training sessions, team meetings, or executive briefings.Use cases for this presentation are vast and varied. Development teams can leverage it to enhance their understanding of secure coding practices, ensuring that security is integrated into the software development lifecycle. IT security professionals can utilize the slides to present risk assessments and mitigation strategies to stakeholders, fostering a culture of security awareness across the organization. Additionally, organizations can adapt the content for workshops, webinars, or conferences, promoting best practices in app security to a wider audience. With our App Security PowerPoint presentation, youll have the tools needed to educate, inform, and inspire action towards a more secure application environment, ultimately protecting your organizations data and reputation in an increasingly digital world.

Organizational Cloud App Security Architecture
This slide provides a cloud app security architecture that enables enterprises to protect applications and data in collaborative cloud environments. Key components are cloud access, log collection, app control, etc. Presenting our set of slides with Organizational Cloud App Security Architecture. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Saas Cloud, Managed Devices, Cloud App Security.
This slide provides a cloud app security architecture that enables enterprises to protect applications and data in collaborative cloud environments. Key components are cloud access, log collection, app control, etc.
- Managed Devices
- Cloud App Security
Related Products

Core Mobile App Security Features Mobile Security
This slide highlights the core features of mobile app security which includes sandbox isolation, robust application framework, user granted permissions, etc. Introducing Core Mobile App Security Features Mobile Security to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Introduction, Ransomware, Fileless Malware using this template. Grab it now to reap its full benefits.
This slide highlights the core features of mobile app security which includes sandbox isolation, robust application framework, user granted permissions, etc.
- Introduction
- Fileless Malware
Web app security model powerpoint slide deck
Presenting web app security model powerpoint slide deck. This is a web app security model powerpoint slide deck. This is a five stage process. The stages in this process are web browser, veracode discovery, external code, uncover and retire, inventory.
Our Web App Security Model Powerpoint Slide Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
- web browser
- Veracode Discovery
- External Code
- Uncover And Retire
Main Types Of Web App Security
This slide discusses the various techniques of web app security such as dynamic application security test, runtime application security protection, etc. Presenting our set of slides with name Main Types Of Web App Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Dynamic Application Security Test, Static Application Security Testing, Interactive Application Security Testing.
This slide discusses the various techniques of web app security such as dynamic application security test, runtime application security protection, etc.
- Dynamic Application Security Test
- Static Application Security Testing
- Interactive Application Security Testing


Cloud App Security Dashboard For An Enterprise
Introducing our Cloud App Security Dashboard For An Enterprise set of slides. The topics discussed in these slides are Activities Monitored, Governance Actions, Files Monitored. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience
Our Cloud App Security Dashboard For An Enterprise are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
- Activities Monitored
- Governance Actions
- Files Monitored
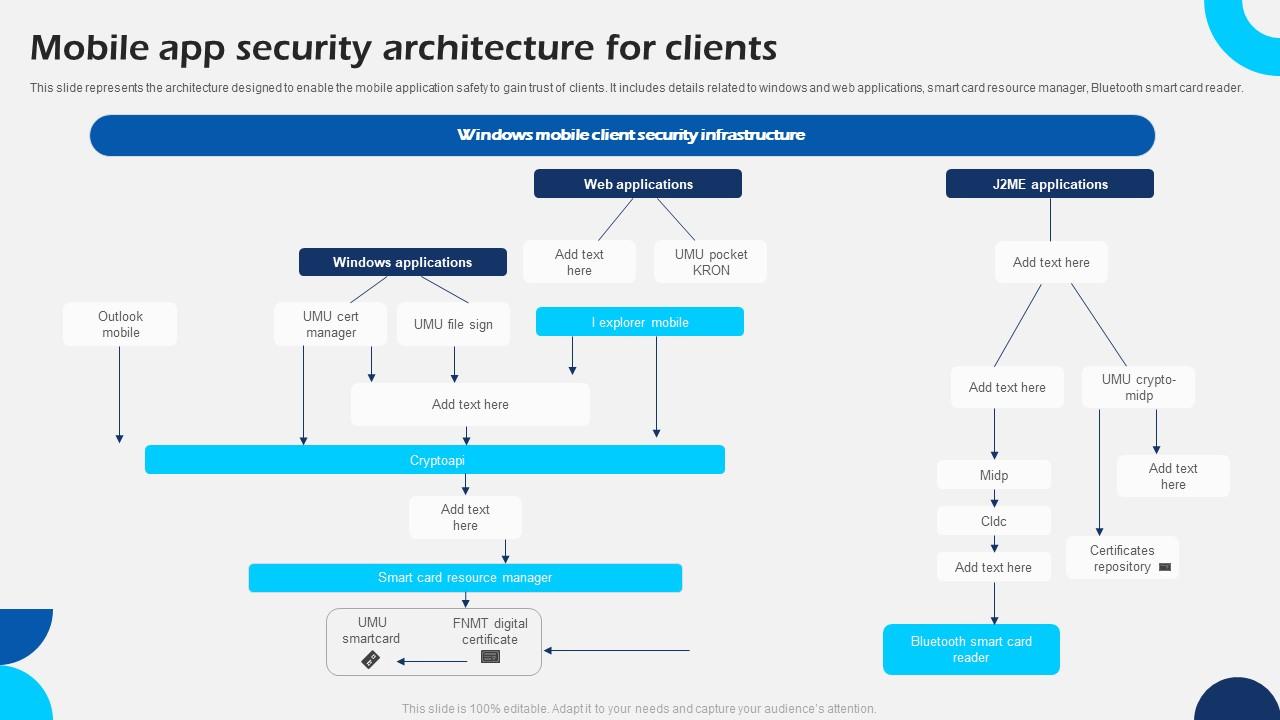
Mobile App Security Architecture For Clients
This slide represents the architecture designed to enable the mobile application safety to gain trust of clients. It includes details related to windows and web applications, smart card resource manager, Bluetooth smart card reader. Presenting our well structured Mobile App Security Architecture For Clients. The topics discussed in this slide are Web Applications, Windows Applications, Security Infrastructure. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
This slide represents the architecture designed to enable the mobile application safety to gain trust of clients. It includes details related to windows and web applications, smart card resource manager, Bluetooth smart card reader.
- Web Applications
- Windows Applications
- Security Infrastructure
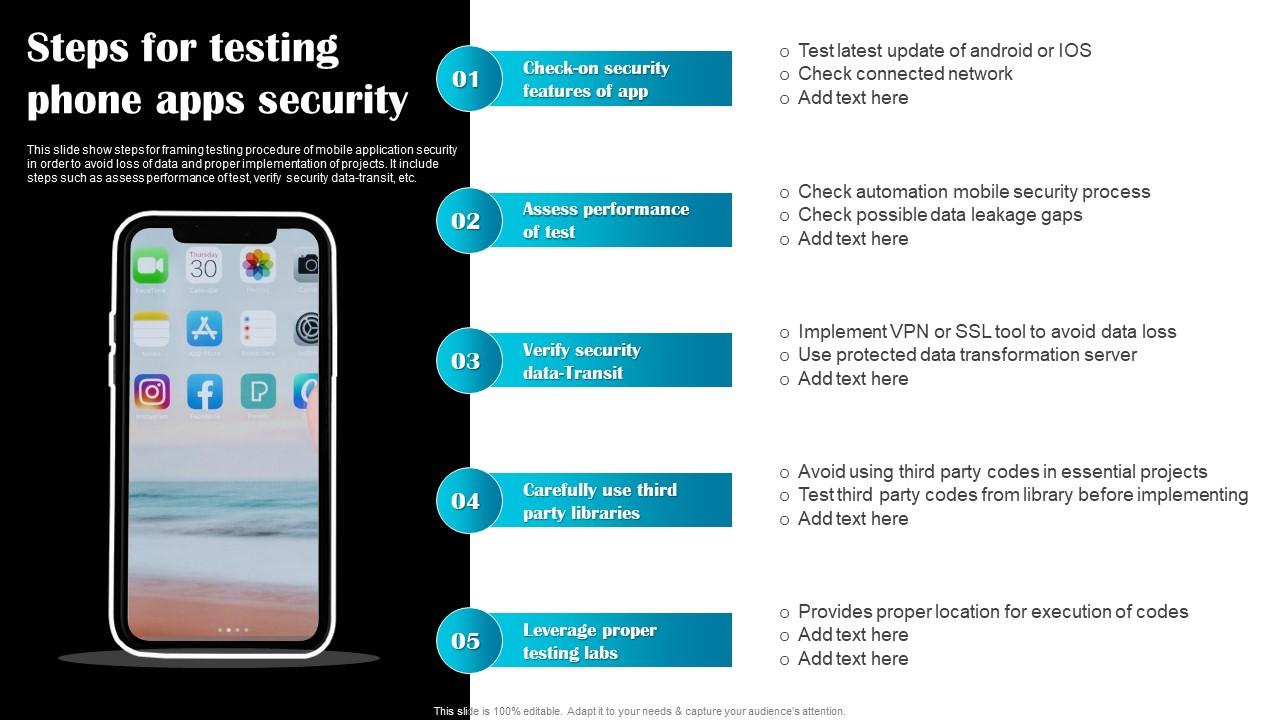
Steps For Testing Phone Apps Security
This slide show steps for framing testing procedure of mobile application security in order to avoid loss of data and proper implementation of projects. It include steps such as assess performance of test, verify security data transit, etc. Presenting our set of slides with Steps For Testing Phone Apps Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Check Security Features, Assess Performance Test.
This slide show steps for framing testing procedure of mobile application security in order to avoid loss of data and proper implementation of projects. It include steps such as assess performance of test, verify security data transit, etc.
- Check Security Features
- Assess Performance Test

Common Issues Affecting Mobile App Security Mobile Security
This slide represents the common issues affecting mobile app security which includes data exposure risks, unencrypted data transmissions, etc. Introducing Common Issues Affecting Mobile App Security Mobile Security to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Stolen Passwords, Phishing Attempts, Social Engineering using this template. Grab it now to reap its full benefits.
This slide represents the common issues affecting mobile app security which includes data exposure risks, unencrypted data transmissions, etc.
- Stolen Passwords
- Phishing Attempts
- Social Engineering
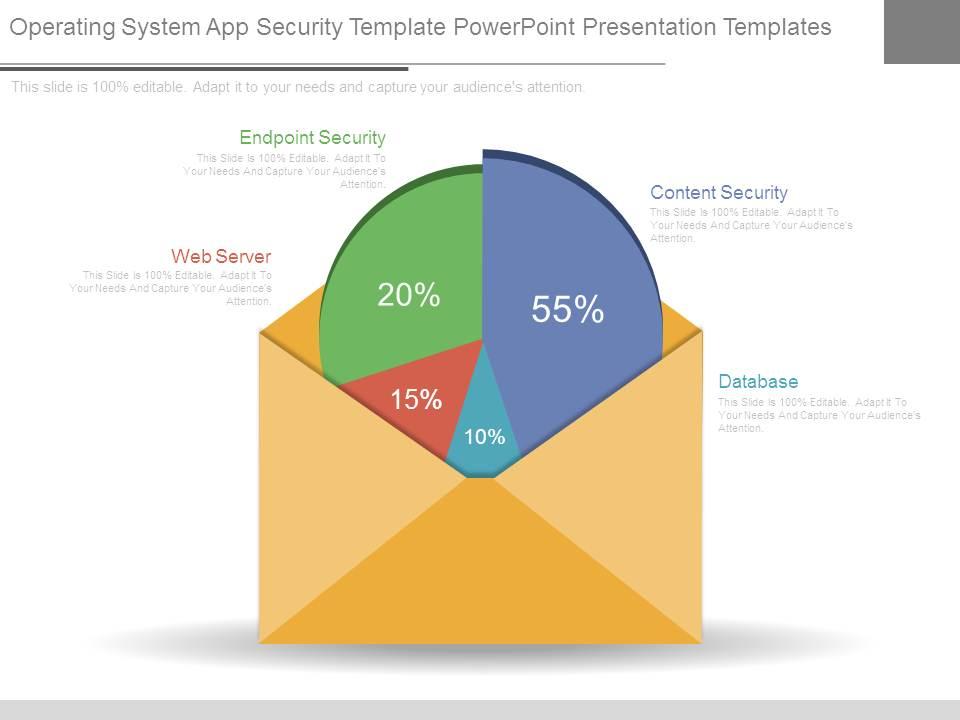
Operating system app security template powerpoint presentation templates
Presenting operating system app security template powerpoint presentation templates. Presenting operating system app security template powerpoint presentation templates. This is a operating system app security template powerpoint presentation templates. This is a four stage process. The stages in this process are web server, endpoint security, content security, database.
Face the brunt of change with our Operating System App Security Template Powerpoint Presentation Templates. You will emerge better for it.
- Endpoint Security
- Content Security

Web app security testing ppt powerpoint presentation designs cpb
Presenting this set of slides with name Web App Security Testing Ppt Powerpoint Presentation Designs Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Web App Security Testing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Our Web App Security Testing Ppt Powerpoint Presentation Designs Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
- Web App Security Testing


IMAGES