Power at Your Fingertips: What is Empowerment Technology and How is it Changing Our World?
By: Author Valerie Forgeard
Posted on Published: June 28, 2023 - Last updated: July 25, 2023
Categories Technology
In today’s fast-paced world, where technology is constantly evolving, empowerment technology refers to any tool or system that enables individuals and communities to take control of their lives, make informed decisions, and ultimately enhance their well-being.
These technologies allow you to shape your future by breaking down barriers and creating opportunities for personal growth.
Imagine a world where you can access life-changing information at your fingertips, enabling you to make well-informed decisions on education, health, finances, and more.
This is precisely what empowerment technology aims to achieve – providing you with the necessary tools and resources to break free from limitations imposed by traditional systems.
By harnessing the power of these innovative technologies, you can unlock your full potential and pave the way for a brighter future for yourself and those around you.
So read on to discover how this revolutionary concept can transform your life imaginatively!

Key Takeaways
- Empowerment technology empowers individuals and communities to take control of their lives, make informed decisions, and enhance their well-being through tools and strategies designed to enhance skills, knowledge, and access to resources.
- Rapid advancements in today’s digital world provide unparalleled opportunities for individuals and communities to access information, collaborate, and make lasting changes.
- Empowerment technology has numerous benefits for individuals and communities, including improved access to education, economic growth, and enhanced civic engagement. It contributes to creating a more inclusive society where everyone has equal opportunities.
- Challenges and pitfalls of empowerment technology include accessibility and affordability, digital literacy and training, and privacy and security concerns. Still, responsible use of technology can be a force for good when used ethically and responsibly.
Definition of Empowerment Technology
You’ll find that empowerment technology refers to tools and strategies designed to help you enhance your skills, knowledge, and access to resources, ultimately giving you more control over your life and decisions.
This kind of technology is all about enabling you to realize your full potential and harness it for personal growth or community development. With the rapid advancements in today’s digital world—including social media platforms, educational websites, online communities, apps, software programs—you now have unparalleled opportunities at your fingertips.
By embracing empowerment technology, you can break free from traditional limitations and tap into a world of endless possibilities. Imagine having access to vast amounts of information that can help you learn new skills or improve existing ones.
Think about the ways in which technology connects us with people from diverse backgrounds who share our interests and passions—forming networks where we can exchange ideas and support each other’s goals. It’s an exciting time for self-improvement, as we’re no longer confined by geographic boundaries or lack of resources; instead, we can seek out the information we need right from our smartphones or laptops.
The Evolution of Empowerment Technology
Let’s explore the fascinating evolution of empowerment technology, from traditional media to the digital platforms we know today.
With the rise of the internet and social media, we’ve gained unprecedented access to information and tools that empower us like never before.
Join this discussion as we delve into how these advancements have transformed our lives, enabling us to connect, create, and collaborate on a global scale.
From traditional media to digital platforms
Transitioning from traditional media to digital platforms has revolutionized the way we consume and share information, ultimately boosting empowerment technology’s impact on society. The shift from newspapers, radio, and television to social media, blogs, and streaming services has not only made it easier for people to access content but also provided them with a platform to voice their opinions and connect with others around the world. This connection fosters a sense of freedom as individuals can now express themselves without any geographical or institutional boundaries.
The table below highlights some key differences between traditional media and digital platforms:
As you can see, digital platforms offer countless advantages over traditional media when it comes to accessibility, interactivity, cost efficiency, censorship resistance, and community building. These factors contribute significantly to the empowering nature of new technologies.
The role of the internet and social media
Imagine the vast possibilities that the internet and social media have unlocked for you, connecting with people across the globe, discovering new ideas, and amplifying your voice in ways never before possible. The role of the internet and social media in empowerment technology cannot be overstated as they have transformed how we communicate, learn, work, and create change.
- Connecting with like-minded individuals: Social media platforms enable you to find others who share your interests or beliefs, fostering community and support.
- Access to information: The internet has democratized access to knowledge, breaking down barriers that once limited those who could learn about particular topics or gain specific skills.
- Amplifying voices: Through social media platforms like Twitter or Facebook, even those without traditional influence can reach a broad audience with their message when it resonates with others.
- Collaboration at scale: Online tools such as Google Docs or Slack facilitate collaboration among people from different locations or time zones in real-time.
Embrace these powerful tools to help realize your dreams and potential – connect with others who share your passion for freedom; dive deep into resources that empower you to make informed decisions; use your online presence to raise awareness for causes close to your heart; collaborate on projects that fuel change in our world.
Examples of Empowerment Technologies
Through empowerment technologies, we’re able to break barriers and uplift communities, enabling individuals to unleash their full potential and make lasting change.
One powerful example is the rise of e-learning platforms such as Coursera, edX, and Udemy. These websites provide access to quality education from prestigious institutions across the globe, giving people who may not have had the opportunity otherwise a chance to gain new skills and expertise. This not only empowers them on an individual level but also contributes to the overall growth and development of their communities.
Another empowering technology worth mentioning is crowdfunding platforms like Kickstarter and Indiegogo. These sites enable creators from all walks of life to pitch their innovative ideas, products or projects directly to consumers who can then choose whether or not they wish to financially support those ideas in exchange for rewards or equity. By bypassing traditional gatekeepers such as banks and investors, these platforms empower individuals with great ideas but limited financial resources to bring their visions into reality – transforming lives in the process.
The power of mobile banking apps also cannot be underestimated when it comes to transformative potential. With just a smartphone in hand, anyone can now manage their finances remotely without having to rely on physical banks – which can be particularly liberating for those living in remote areas or lacking proper documentation for traditional banking services.
This newfound financial independence allows people even greater control over their economic future – fostering entrepreneurial spirit and encouraging growth within local economies that might have otherwise been stifled by bureaucratic red tape.
Benefits of Empowerment Technology
Empowerment technology is designed to put power back into the hands of the people, enabling them to take control of their own lives and make informed decisions about their future.
By providing access to information, resources, and opportunities, empowerment technology paves the way for greater personal freedom and self-determination. This, in turn, leads to numerous benefits such as:
- Improved access to education and learning resources: With empowerment technology, you can obtain knowledge from anywhere at any time. Digital libraries, online courses, and educational apps make it easier for people in remote areas or those with limited mobility to continue growing their skills.
- Economic growth: As more people gain access to digital tools that allow them to connect with businesses around the world, they’re able to create new income streams for themselves or expand on existing ones.
- Enhanced civic engagement: Technology empowers citizens by giving them platforms where they can voice their opinions on important issues or organize grassroots movements for change.
By embracing empowerment technology, you’re not only unlocking your own potential but also contributing towards creating a more inclusive society where everyone has equal opportunities. The ripple effect extends far beyond personal gains – as individuals become more empowered through this technology, they are better equipped to contribute positively within their communities.
This can leads to overall development at local, national, and even global levels – truly exemplifying how each person’s journey towards freedom can impact countless others along the way.
Empowerment Technology in Education
Imagine advancing your education through online courses and degree programs, while enhancing your digital literacy skills at the same time.
You can experience the benefits of empowerment technology in education, with virtual classrooms and tutoring that cater to various learning styles and schedules.
Don’t miss out on this opportunity to transform your educational journey with cutting-edge tools and resources designed to empower you every step of the way.
Online courses and degree programs
Dive into a world of endless possibilities with online courses and degree programs, boosting your skills and knowledge at your own pace. The digital age has unlocked doors to countless opportunities for personal and professional growth through empowerment technology.
With various platforms offering an array of courses, you can now take charge of your education by choosing the subjects that pique your interest or advance your career without being confined by traditional classroom settings. Empower yourself through these accessible online resources:
- Flexible learning schedules allow you to maintain a healthy balance between work, family commitments, and studies.
- Networking opportunities help you connect with like-minded individuals from all over the world who share similar passions.
- Personalized learning experiences enable you to focus on areas where you need improvement or explore new topics tailored to your interests.
- Cost-effective options make higher education more accessible, eliminating barriers such as exorbitant tuition fees and living expenses associated with attending college in person.
By embracing online courses and degree programs powered by empowerment technology, you’re not only investing in yourself but also unlocking a newfound sense of freedom. Seize this opportunity to redefine what learning means to you while taking control of your future.
Digital literacy initiatives
As you continue to explore the world of empowerment technology, it’s essential not only to acquire new skills and knowledge through online courses and degree programs but also to develop your digital literacy. This aspect of empowerment technology ensures that you can effectively navigate the digital landscape and make informed decisions on how to utilize various tools and resources at your disposal, ultimately granting you more freedom in your personal and professional life.
Digital literacy initiatives play a crucial role in empowering individuals like yourself by providing access to essential digital skills, information, and opportunities. By participating in these initiatives, you’ll learn how to use different technologies responsibly, communicate effectively online, assess the credibility of various sources of information, protect your privacy and security while using the internet, among other valuable skills.
As an empowered digital citizen with strong digital literacy skills, you’re better equipped to seize opportunities for growth personally or professionally. Embrace this newfound freedom as you engage confidently with the ever-evolving world of technology!
Virtual classrooms and tutoring
You’ll find that virtual classrooms and tutoring offer an engaging and convenient way to expand your knowledge, fostering personal growth and professional development. The flexibility of learning online allows you to access a wide range of courses and resources at your fingertips, giving you the freedom to learn at your own pace and on your own terms.
Consider these benefits of virtual classrooms and tutoring:
- Flexibility : Learn on your schedule, balancing work, family, and other commitments.
- Accessibility : Access educational materials anytime, anywhere – all you need is an internet connection.
- Personalized Learning : Tailor your education to meet specific needs or goals through customized lessons or tutoring sessions.
- Cost-effective : Save money by eliminating the need for travel or expensive textbooks while often gaining access to free or lower-cost resources.
- Collaboration Opportunities : Interact with instructors, tutors, and fellow students from around the world in real-time discussions or forums.
By embracing virtual classrooms and tutoring as part of your learning journey, you can unlock new doors to opportunities that may have been previously out of reach. Empower yourself with this innovative technology to elevate both your personal growth and career advancement.
Empowerment Technology in Healthcare
In healthcare, empowerment technology enables you to take charge of your own well-being by providing access to information, tools, and resources for better decision-making. This means you can easily monitor your health, track progress, and make informed choices in consultation with your healthcare providers.
With the advent of wearables, telehealth services, and online health platforms, maintaining a healthy lifestyle has never been more accessible or efficient. With empowerment technology at your fingertips, you’re no longer confined by traditional healthcare limitations – instead, you have the freedom to explore various options that best suit your individual needs.
For instance, telemedicine allows you to consult with medical professionals remotely through video calls or messaging services. This not only saves time but also helps overcome geographical barriers when seeking specialized care. Additionally, mobile apps provide personalized guidance on managing chronic conditions such as diabetes or hypertension while promoting a proactive approach towards preventive care.
By embracing these technological advancements in healthcare delivery and management systems, you can actively participate in shaping your own health journey. Empowerment technology fosters an environment where individuals are better equipped to make informed decisions about their physical and mental well-being.
So go ahead – seize control of your health destiny; it’s right there waiting for you!
Empowerment Technology in Business
With today’s digital tools at your disposal, you’re able to revolutionize the way you run and grow your business like never before. Empowerment technology in business allows you to streamline operations, enhance customer experiences, and make data-driven decisions that will ultimately lead to increased revenue and growth. By embracing these technological advancements, you’re giving yourself the freedom to focus on what matters most – providing exceptional products or services while growing a sustainable and successful brand.
Empowerment technology can manifest in several ways within the world of business:
- Automating repetitive tasks: Free up valuable time for your employees by automating mundane tasks such as invoicing, payroll management, or data entry.
- Enhancing communication: Utilize tools like Slack or Microsoft Teams to keep employees connected and informed in real-time.
- S treamlining project management: Platforms like Asana or Trello enable teams to collaborate effectively on projects while maintaining visibility into progress and deadlines.
- Leveraging data analytics: Make better-informed decisions based on data trends through systems such as Google Analytics or Tableau.
- Expanding marketing reach: Take advantage of social media platforms, email campaigns, and SEO strategies to increase brand visibility and attract new customers.
As you incorporate empowerment technology into your business processes, remember that it’s not just about making things more efficient – it’s also about creating an environment where both employees and customers feel valued.
Empowerment Technology for Social Change
Harnessing the power of digital tools can truly revolutionize the way we create lasting social change, inspiring communities to unite and make a difference together. Empowerment technology enables individuals and groups to connect, share ideas, and collaborate on projects aimed at addressing pressing societal issues. From promoting gender equality to combating climate change, empowerment technology is instrumental in amplifying voices that have been silenced or marginalized for far too long.
To better understand how empowerment technology impacts social change, take a look at this table highlighting various tools, their purpose, and examples:
Empowerment technologies play an increasingly important role in driving social change by facilitating communication between like-minded individuals who are passionate about making a difference. It’s essential that organizations continue developing innovative digital solutions that help empower citizens worldwide, ultimately creating more resilient societies where everyone has access to the same opportunities.
Empowerment Technology and Inclusivity
You’ll find that digital tools can play a crucial role in fostering inclusivity, bridging gaps between diverse communities and ensuring equal access to resources and opportunities for all. Empowerment technology isn’t just about providing new ways to communicate or collaborate; it’s also about breaking down barriers and creating an inclusive environment where everyone can thrive.
By leveraging the power of these technologies, you can help promote a more inclusive society where diversity is celebrated and valued. So, embrace this powerful movement today and take your first steps towards shaping a brighter future filled with possibilities limited only by imagination!
Here are three ways that empowerment technology can be used to promote inclusivity:
- Empower marginalized communities : Empowerment technology provides platforms that give voice to those who may have been previously unheard or overlooked due to social, economic, or geographic constraints. This leads to increased awareness of their struggles, allowing for better support systems and advocacy efforts.
- Enhance accessibility : Digital tools make it easier for people with disabilities to participate in various aspects of life by offering assistive technologies like screen readers, speech-to-text software, and adaptive hardware. These innovations contribute significantly towards leveling the playing field for individuals with diverse needs.
- Promote cross-cultural understanding : Social media platforms enable people from different backgrounds to connect with one another and learn from each other’s experiences. This fosters greater empathy, understanding, and respect for different perspectives.
By embracing empowerment technology as a tool for promoting inclusivity, you’re actively contributing towards building a more open-minded world where everyone has the chance to be heard and succeed on their own terms. You’ll witness firsthand how empowerment technology inspires hope in the face of adversity while empowering individuals from all walks of life to seize control over their futures – whether that means starting businesses, pursuing education, or advocating for social change within their communities.
Challenges and Pitfalls of Empowerment Technology
While it’s true that digital tools can significantly impact inclusivity and empowerment, there are also challenges and pitfalls to consider when implementing these innovations. As you navigate the world of empowerment technology, it’s essential to be aware of potential obstacles and plan for ways to overcome them. By doing so, you’ll be better equipped to harness the power of technology while minimizing any negative consequences.
One primary challenge is ensuring accessibility and affordability for all users, as limited access or high costs may exclude certain individuals from benefiting from these technologies. This could inadvertently exacerbate existing inequalities within society. Additionally, fostering digital literacy and providing adequate training is crucial in empowering individuals to confidently use these tools. Without proper support, some may become overly dependent on technology or struggle to adapt if technological advancements outpace their skillset. Lastly, privacy and security concerns are paramount; misuse of personal data is a serious risk that must be addressed in the development and implementation of any new tool.
As advocates for empowerment through technology, it’s vital not only to promote its benefits but also address the challenges head-on. By acknowledging these issues and actively seeking solutions that prioritize inclusivity, privacy, and education at every stage of development, you’ll contribute positively towards a future where everyone has equal access to opportunities facilitated by innovative digital tools.
Empowerment Technology and Ethics
As you navigate the world of empowerment technology, it’s crucial to consider not only its potential benefits but also the ethical implications surrounding its use.
Strive for responsible utilization of these tools by balancing innovation with social responsibility. Ensure that your technological advancements contribute positively to society while minimizing any negative impacts.
Remember, the power of technology can be a force for good when used ethically and responsibly.
Responsible use of technology
It’s essential to practice responsible use of technology, ensuring that we harness its empowering potential without causing harm or perpetuating negative behavior. By using technology responsibly, you not only protect yourself but also contribute to a better digital environment for everyone. When you’re mindful of your actions and their consequences, you can enjoy the freedom and opportunities that come with empowerment technology.
To paint a picture for you on responsible use of technology, consider these four key aspects:
- Privacy : Be cautious about sharing personal information online and always check privacy settings on social media platforms. Protect your data by using strong passwords and updating them regularly.
- Digital etiquette : Treat others with respect in online interactions, just as you would in person. Avoid engaging in cyberbullying or spreading harmful content.
- Information literacy : Learn how to identify reliable sources of information and be critical of what you read or share online. This will help prevent the spread of misinformation and ensure informed decision-making.
- Sustainable practices : Minimize the environmental impact of your tech usage by recycling electronic waste properly, reducing energy consumption where possible, and supporting companies that prioritize sustainability.
By incorporating these principles into your daily life, you’ll become an advocate for responsible use of technology while enjoying the freedom it provides at the same time!
Balancing innovation with social responsibility
Striking the perfect balance between cutting-edge innovation and social responsibility can be a challenging tightrope to walk, but when done right, it paves the way for a brighter, more inclusive future.
As you navigate through this interconnected world, it’s crucial to keep in mind that embracing new technologies shouldn’t come at the expense of societal well-being. Be an advocate for ethical practices within your industry and strive to make decisions that prioritize both progress and compassion.
By taking into account the potential consequences of your actions on vulnerable communities and the environment, you’ll be contributing to a world where technology empowers everyone – without leaving anyone behind.
To achieve this delicate balance, consider adopting a proactive approach towards assessing the impact of your innovations. Engage with diverse perspectives by involving stakeholders from different backgrounds in decision-making processes and collaborate with experts who can provide valuable insights on potential risks or concerns.
Don’t shy away from asking tough questions about how your work may affect society at large – these discussions will help ensure that you’re not just pushing boundaries blindly but are also considering their broader implications.
In doing so, you can harness the power of empowerment technology while remaining accountable and socially responsible – ultimately helping to create a world where freedom flourishes alongside progress.
Empowerment Technology and the Environment
Harnessing empowerment technology can significantly help protect our environment, making it easier for us to adopt eco-friendly practices and work towards a greener future. By leveraging innovative tools and solutions, you can actively participate in reducing your carbon footprint and promoting sustainable living. Empowerment technology has the potential to revolutionize how we approach environmental challenges by offering new ways to conserve resources, monitor ecosystems, and spread awareness about ecological issues.
Some of the ways empowerment technology contributes to environmental protection include:
- Smart grids: These energy management systems optimize power distribution and consumption, reducing overall energy usage.
- Remote sensing technologies: Satellite imagery and drones allow us to monitor deforestation, track endangered species, and assess the impact of natural disasters on ecosystems.
- Eco-friendly apps: From carpooling services to zero-waste grocery shopping platforms, these applications facilitate environmentally conscious choices in our daily lives.
As you continue exploring the world of empowerment technology, remember that every individual action counts when it comes to preserving our planet. By embracing these advancements in your life – whether through supporting renewable energy initiatives or using eco-friendly products – you’re taking an important step towards a more sustainable future.
The power lies within each one of us; together, let’s harness this potential for change and create a cleaner, greener Earth for generations to come.
The Future of Empowerment Technology
Envisioning the future of tech-driven empowerment, we’re likely to witness a colossal transformation in how individuals and communities access opportunities, overcome challenges, and shape their destinies. With rapid advancements in fields such as artificial intelligence, blockchain, and virtual reality, the landscape of human interaction will change dramatically.
As a result, you’ll have more control over your personal growth and development than ever before. The democratization of technology will enable people from all walks of life to harness its power for their own personal advancement. Imagine having access to resources that allow you to learn new skills at your own pace or collaborate with others across the globe without any barriers.
The possibilities are endless: from remote learning platforms that provide equal educational opportunities for everyone – regardless of location or socioeconomic status – to decentralized financial systems that give people greater control over their finances and economic well-being. You’ll be able to tap into these resources like never before.
As empowerment technology continues to evolve and become even more accessible, it’s crucial for you not only to embrace this shift but also actively participate in shaping its direction. By staying informed about emerging trends and engaging with innovative tools that foster self-improvement and meaningful connections with others, you can help create a world where everyone has the freedom to pursue their dreams on an equal footing.
Empowerment Technology Policy and Regulation
As you delve into the world of empowerment technology policy and regulation, consider the crucial role that government initiatives and support play in fostering innovation and growth.
Recognize the importance of legal frameworks and guidelines in providing a safe, ethical, and equitable environment for all stakeholders involved.
Stay informed about these key aspects to fully understand how they shape the future of empowerment technology and its potential to transform society for the better.
Government initiatives and support
You’ll be amazed by how government initiatives and support can uplift communities, fueling their growth through the power of empowerment technology. By leveraging technology to improve access to information, resources, and opportunities, governments worldwide are fostering an environment where individuals can thrive and find the freedom they desire.
Here are just a few examples of how governments are making strides in promoting empowerment technology:
- Many countries have established National Information and Communications Technology (ICT) policies designed to bridge digital divides and promote widespread adoption of new technologies.
- In some regions, local governments provide free public Wi-Fi hotspots in areas with limited internet access, enabling citizens to stay connected and informed.
- Various government-sponsored programs aim to teach digital literacy skills to disadvantaged populations, helping them become more self-sufficient in today’s increasingly digital world.
- Some governments also offer incentives for businesses embracing empowerment technologies as part of their core operations or corporate social responsibility initiatives.
By supporting these types of initiatives, governments play a crucial role in creating digitally inclusive societies that empower citizens with the tools necessary for personal growth and development.
Through continued investment in these programs, we can work towards building a world where everyone has equal access to the opportunities that come with embracing technology – ultimately ensuring greater freedom for all.
Legal frameworks and guidelines
Imagine navigating the complex world of legal frameworks and guidelines that play a vital role in promoting digital inclusion and protecting your rights in the age of information.
As you venture into this realm, you’ll find that these legal structures are essential for creating an environment where empowerment technology can thrive. They foster innovation, provide resources to bridge the digital divide, and safeguard users from potential harm while enabling them to harness the transformative power of technology.
Having a clear understanding of these legal frameworks and guidelines is crucial if we wish to fully embrace the opportunities presented by empowerment technology. By becoming knowledgeable about relevant laws and regulations, you can confidently navigate this digital landscape, ensuring that your actions align with established norms while also advocating for changes when necessary.
Empowerment Technology Success Stories
There’s nothing quite like hearing real-life success stories of individuals who’ve harnessed the power of empowerment technology to overcome challenges and improve their lives. These inspiring examples demonstrate how technology can be a catalyst for positive change, enabling people from all walks of life to take control of their own destinies and achieve their goals.
- M-Pesa : This mobile money transfer service in Kenya has revolutionized financial inclusion, allowing millions of unbanked citizens access to banking services through their mobile phones. It has empowered rural communities, small businesses, and individuals by providing them with secure, fast, and affordable financial transactions.
- Kiva : A global crowdfunding platform that connects entrepreneurs in developing countries with lenders worldwide. Kiva empowers these entrepreneurs by giving them access to capital they wouldn’t otherwise have, enabling them to grow their businesses and improve their communities.
- Duolingo : A free language learning app that empowers users by making education accessible to everyone. Through gamification techniques and personalized learning experiences, Duolingo helps millions learn new languages every day.
- EdX : An online learning platform that offers high-quality courses from top universities around the world at no cost or low cost. EdX empowers learners by providing flexible educational opportunities that are accessible regardless of location or income level.
- Solar Sister : A social enterprise that trains women in sub-Saharan Africa as solar energy entrepreneurs. By equipping these women with knowledge about clean energy products and business skills, Solar Sister is empowering them to become agents of change within their communities while also addressing critical issues such as climate change and gender inequality.
As you can see from these remarkable stories, empowerment technology truly has the potential to transform lives in profound ways.
By breaking down barriers and opening up new opportunities for personal growth, this innovative field is helping countless individuals realize the freedom they so deeply desire. So whether it’s through financial services or education platforms or sustainable energy solutions, empowerment technology is paving the way for a brighter and more equitable future for all.
- Research article
- Open access
- Published: 23 February 2021
Technology as the key to women’s empowerment: a scoping review
- April Mackey ORCID: orcid.org/0000-0002-7069-5843 1 &
- Pammla Petrucka 1
BMC Women's Health volume 21 , Article number: 78 ( 2021 ) Cite this article
29k Accesses
24 Citations
19 Altmetric
Metrics details
Information and communications technologies (ICTs) have empowered people to communicate and network at a global scale. However, there is lack of in-depth understanding of the use of ICTs for women's empowerment. This study examines how the concept empowerment is defined, utilized and measured in research studies, the existing evidence on the use of ICTs for women’s empowerment and the gaps in knowledge at the global level.
The authors’ conducted a scoping review using the Arksey and O’Malley methodology. The search identified papers from ten databases, including Scopus, Embase, ABI Inform, Soc Index, Sociological Abstracts, Gender Studies, Springer Link, PsychInfo, Science Direct, and Academic Search Complete over the period of 2012–2018. Search criteria included articles that focused on women’s empowerment and utilized technologies as interventions. Out of a total of 4481 articles that were initially identified, 51 were included.
Technology played a variety of roles in supporting the development of women’s capacities and resources. Results revealed the use of ICT interventions in the overarching areas of outreach (e.g., health promotion), education (e.g., health literacy opportunities), lifestyle (e.g., peer coaching and planning), prevention (e.g., screening opportunities), health challenges (e.g., intimate partner violence apps), and perceptions of barriers (i.e., uptake, utilization and ubiquity to ICTs for women). Despite the positive use of technology to support women in their daily lives, there was a lack of consensus regarding the definition and use of the term empowerment. The concept of empowerment was also inconsistently and poorly measured in individual studies making it difficult to determine if it was achieved.
This scoping review provides a comprehensive review of current and emerging efforts to use ICTs to empower women. The findings suggest a need for collaborative efforts between researchers, program implementers and policy makers as well as the various communities of women to address the persistent gender disparities with respect to ICTs.
Peer Review reports
The term women’s empowerment emerged in the 1970s in response to the need for social justice and gender equality [ 1 , 2 ]. As the term evolved in the 1990s, it was increasingly applied to women who were oppressed and lacking the freedom of choice and action to shape their lives, as well as to discuss women’s participation across multiple sectors in society. More recently it has been used as an outcome and a goal to be achieved is to balance the scales of gender equality and equity. For this research, the definition used regarding women’s empowerment is a process by which women who have experienced oppression acquire the ability to make autonomous and strategic life choices based on their personal priorities. Empowerment is achieved when a woman has the resources, agency, and capabilities to execute decisions on matters of importance [ 3 , 4 ].
Globally women are more likely to experience less favourable social determinants of health (such as over-representation of women in low-paying, insecure employment; lower education and literacy levels amongst rural and immigrant women) than their male counterparts. Women carry the bulk of responsibility for raising children and meeting household obligations, which, globally, contribute to this continued disadvantage [ 5 , 6 , 7 ]. Due to a lack of affordable and quality daycare, women are over-represented in part-time work force, and often remain within low-income bracket [ 5 , 6 , 7 , 8 ]. Gender, as a social determinant of health, is influenced by the “gendered” norms of the roles, personality traits, attitudes, relative power, and influence that society ascribes to it [ 9 , 10 ]. The transition from the Millennium Development Goals to the Sustainable Development Goals (SDGs) in 2015 saw the emergence of Target 5 which aims to “Achieve gender equality and empower all women and girls” (p. 20) [ 11 ]. A major SDG indicator supporting attainment of women’s empowerment is “enhancing the use of enabling technology by increasing the proportion of women and girls who have access” (p. 20) [ 11 ].
Information and communication technologies (ICTs) have catalyzed communication and networking between and among people on a global scale. However, as ICTs have become ubiquitous and grown in both type and access, a digital divide has emerged. This divide parallels gaps in social contexts, such as income and education, as those who use and benefit from access to technologies often have other resources more readily available [ 12 ]. This divide widens the inequity and inequality gaps based on gender, age, disability, or socioeconomic status [ 13 , 14 ].
Women’s empowerment and ICTs have been the subject of global goals, discussions, and debates for many decades [ 15 , 16 ]. Global discussions, such as the 1995 World Conference on Women: Beijing Declaration and Platform for Action, deliberated and advocated for the inclusion of women in the information society in order to fully achieve women’s empowerment in connection with ICT. In 2013, 200 million more men had access to the internet than women [ 17 ]. Women use ICTs much less frequently and intensely than men [ 18 , 19 , 20 , 21 ] In 2016, the International Telecommunications Union (ITU) stated that the percentage of women gaining access to ICT is actually decreasing—with women utilizing ICTs 11% less than men in 2013 and 12% less than men in 2016 [ 19 ]. The most recent 2018 report indicated that the overall proportion of internet usage for women was 12% lower than men [ 19 ].
The extant evidence lacks sufficient depth and detail as to exactly how ICTs are being used by women and why they use it less frequently. An important aspect of empowerment in the context of ICTs is gaining a clearer picture as to the type of technologies and technological interventions being used by women. Many authors agree that improved access to ICTs can assist in providing women with employment resources and opportunities that could narrow the gender wage gap, assist in making education and health information more accessible, contribute to the end of violence against women, and lead to women’s empowerment and leadership [ 15 , 22 , 23 , 24 ].
The objectives of this research were to: determine how the concept of empowerment is defined, utilized, and measured in research studies; explore existing evidence regarding the use of ICTs as interventions towards achieving women’s empowerment; and explore the gaps in knowledge and research on this topic from an individual, community, and global perspective.
This research involved a scoping review, which is methodologically similar to a systematic review, to provide a rigourous synthesis of existing evidence [ 25 , 26 ] For the purpose of this study, the scoping review framework used was described by Arksey and O’Malley [ 27 ] as a five-step process with an optional sixth step. These steps include: (1) identifying the research question, as the starting point to guide the search strategy; (2) identifying relevant studies, which involved the development of a comprehensive search strategy to ensure accurate and complete results; (3) selecting studies, which involved developing a-priori inclusion and exclusion criteria that were revised throughout the review process, as familiarity with the evidence increased; (4) charting the data, which involved charting and sorting key material from the results into themes and trends; (5) collating, summarizing, and reporting the results, which involved presenting the results as a narrative; and (6) consulting with relevant stakeholders, which is contingent upon time and resource considerations. For the purposes of this research, the sixth step was not performed.
Review protocol, team, and management
To ensure transparency, rigour, reproducibility, and consistency, protocols were developed prior to the start of the research, for the inclusion criteria, search strategy, and data characterization. This helped to ensure an unbiased approach to the search protocol and to enhance rigour [ 27 ]. These are available upon request. The scoping review was conducted by a team of individuals with multi-disciplinary capabilities in nursing, knowledge synthesis methodologies, and ICTs. The primary reviewers included the lead and co-authors, as well as one research assistant. In addition, a University librarian was consulted throughout the search term selection process to ensure completeness and accuracy of search terms as well as a comprehensive and complete search strategy.
Any and all potentially relevant citations identified throughout all stages were imported into EndNote™, a reference management software, where duplicates were removed by the program and then double checked, and manually removed by the lead author; the list of citations was then imported into a web-based electronic systematic review management platform, DistillerSR™. The screening for article relevance, up to the data extraction stages, were conducted using this software. Two reviewers (i.e., lead author and research assistant) were involved throughout the selection and analysis process to ensure consistency, adherence to the inclusion/exclusion criteria, relevance to the research question, as well as the categorization of data into themes and patterns. As part of this process, all articles were screened by the lead author and research assistant. Any discrepancies were brought forward to the co-author who made an independent decision whether to include or exclude the article.
Review intent and scope
This was part of a broader study aimed at addressing the following question: What is the global impact of ICTs on women’s empowerment? The current review aimed to examine the concept of empowerment, while exploring the evidence on ICTs as interventions for achieving women’s empowerment at the individual, community, and global levels.
Search strategy
The authors ensured identification of relevant and suitable publications by creating a search strategy protocol prior to retrieving evidence from a variety of sources. As per Arksey and O'Malley [ 27 ], the following avenues were reviewed as part of the search strategy: searching relevant electronic databases, reviewing reference lists of pertinent articles to identify additional sources, and manually searching key journals.
To ensure the search was comprehensive, the following databases, available through the University of Saskatchewan library, were searched on November 30, 2016 and updated on January 1, 2018: Scopus, Embase, ABI Inform, Soc Index, Sociological Abstracts, Gender Studies, Springer Link, PsychInfo, Science Direct, and Academic Search Complete. The COCHRANE Library was also searched for any relevant trials in the trial registry. Limits placed on the search included: English only, no book reviews, publications dated 2012–2017, and the protocol was pretested in Scopus and Soc Index using select key words including “women” and “empowerment” and “technology.” An illustration of the search term strategy is presented in Table 1 .
Search terms were drawn from the research question, as well as from lengthy discussions with the university librarian and expanded upon based on a cursory search of two databases. To determine the range and breadth of key terms, an initial limited search of two databases was conducted yielding several papers. These databases were determined in consultation with the university librarian and included Scopus and Gender Studies. These papers were then analyzed for similar keywords, definitions, analogies, and index terms that were relevant synonyms to the initial search words [ 28 , 29 ]. These additional terms were added to a master list that informed the final search strategy. Specifically, for the term empowerment, keywords were chosen that could provide results that included a lack of empowerment as well, thus the inclusion of “barrier” and “disempower”. The other search terms came directly from key articles and databases and were demonstrated to be the most common variations on the term “empower”. An additional term that was used interchangeably with “empower” was “agency”, however, as this term is used more frequently in conjunction with organizations and not empowerment, it was removed from the search term list.
The ability of the electronic database search to identify all relevant primary research was verified by hand searching the reference lists of eight key peer reviewed articles and nine key electronic journals that were flagged through the initial test search as well as the main search. The journals were chosen based on their relevance to the research question as well as their scholarly nature. The initial three identified journals were: Community Informatics , Gender and Development, and Journal of Women in Culture and Society. Subsequent journals were identified and selected for a hand-search once the initial search was completed. These were : Gender, Technology & Development , Computers in Human Behaviour , American Journal of Health Behaviour , American Journal of Public Health , and Women’s Health Issues . These journals were then reviewed for additional articles potentially not identified through the database search; this included entering the general search into journal databases.
Additional grey literature was identified by hand-searching the websites of the Association for Computing Machinery Digital Library Journals and Conference Proceedings, the UN Women, Status of Women Canada, the United Nations Development Program, the International Center for the Research of Women, the Girls Action Foundation, the Information and Communications Technology Council, the ITU, and the International Development Research Center for primary research reports, guidelines, situation reports, and referenced publications that were not already included.
Study selection: relevance screening and inclusion criteria
The focus of the study selection was locating published and unpublished academic articles, which may have any type of study design, including qualitative, quantitative, or mixed methods. The initial pool of results included a total of 4481 citations. An initial set of inclusion and exclusion criteria were developed a-priori to screen abstracts and titles of citations which were refined during each review of the pool of articles. Research articles were initially considered relevant if they included women’s empowerment and/or information and communication technology concepts in the title or abstract of the publication. Synonyms for these concepts were created in consultation with the librarian to ensure a robust search strategy for maximum location and inclusion of studies. Given the evolving nature of ICTs and their role in interventions, the authors wanted the articles to reflect a recent knowledge base, therefore the timeframe of 2012–2016 was chosen, which was later expanded to December 31, 2017 as the review progressed. The results were also filtered to include English only content.
First screen: inclusion criteria
The inclusion criteria created for the first level of study selection were driven by the review topics, specifically, women, empowerment, and ICTs. According to the Joanna Briggs Institute (JBI) (2015), the inclusion criteria should be based on three themes, also known by the acronym of PCC: (a) participant description, (b) concept, which is likened to the phenomena of interest, and (c) context. The inclusion criteria used in the first level of selection were country of publication, date of publication (2012–2017), and the use of both of the following concepts in the title or abstract of the publication: women’s empowerment and/or information and communication technology. At this stage, the lead author looked for the presence of the key words in the title and/or abstract. The use of these keywords as inclusion criteria was designed to be intentionally broad to provide a sense of what publications linked the two concepts (i.e., women's empowerment and ICTs).
First screen: study selection
On first review, the initial pool of articles was subjected to a staged process to ensure studies were selected that were relevant to the research question and met the inclusion criteria. Articles were first excluded based on duplication within the initial search results. This exclusion was conducted using the search tools feature within the electronic database, but also within the reference management program Endnote™ and then manually by the lead author. The inclusion criteria were applied to the title and abstract of the publication. Any title or abstract that did not meet the inclusion criteria was removed from further review and consideration. All articles excluded by the criteria were sent to the research assistant who confirmed the exclusion. Any disagreements or contradictions between the primary author and the research assistant were thoroughly discussed, with both parties having to agree to the inclusion before the publication could be added back into the pool of articles to move on to the next stage. Additionally, if an article could not be excluded based solely on the title or the abstract, the full article was reviewed for relevance to the research question and inclusion criteria. These latter two points did not prove to be an issue as there were no disagreements.
Second screen
The remaining pool of articles was then reviewed a second time by applying a second level of inclusion criteria to the title as well as the abstract. It is common and encouraged as part of the scoping review process to generate increased cumulative familiarity with how concepts are presented within the evidence. This, in turn, informed the decisions that were made regarding the inclusion or exclusion criteria in the subsequent stage. Much of the articles after the first level of elimination included technology as a passive aspect of the study and not one that women actively participated in. It was important for the authors that the technological aspect of each study be an intervention that women could engage in towards building self-efficacy and capacity. This informs current gaps within the evidence that speak to how women are using technologies to support their empowerment. As such, this set of inclusion criteria focused on technology as an intervention and women as active participants in the study instead of just the word “women” found throughout the first set of criteria.
Final screen
For the final review of the full text articles, based on the content and findings in the scoping review process, an additional criterion was included. The authors wanted to explore how the social determinants of health informed and supported the concepts of women, empowerment, and ICTs. At this stage, it was noted which social determinants of health, if any, were present in each article. The list of social determinants based on the Government of Canada (2019) criterion was utilized as a reference for this portion of the process, such as employment and working conditions; income and social status; social supports and coping skills. The remaining 59 articles all had social determinants of health. A subsequent review resulted in 14 of the 59 articles being eliminated from consideration as they did not meet the inclusion/exclusion criteria. Rather than focus on a range of these determinants, the authors decided to include all 45 articles and to then review the implications of this finding in the analysis (Fig. 1 ).
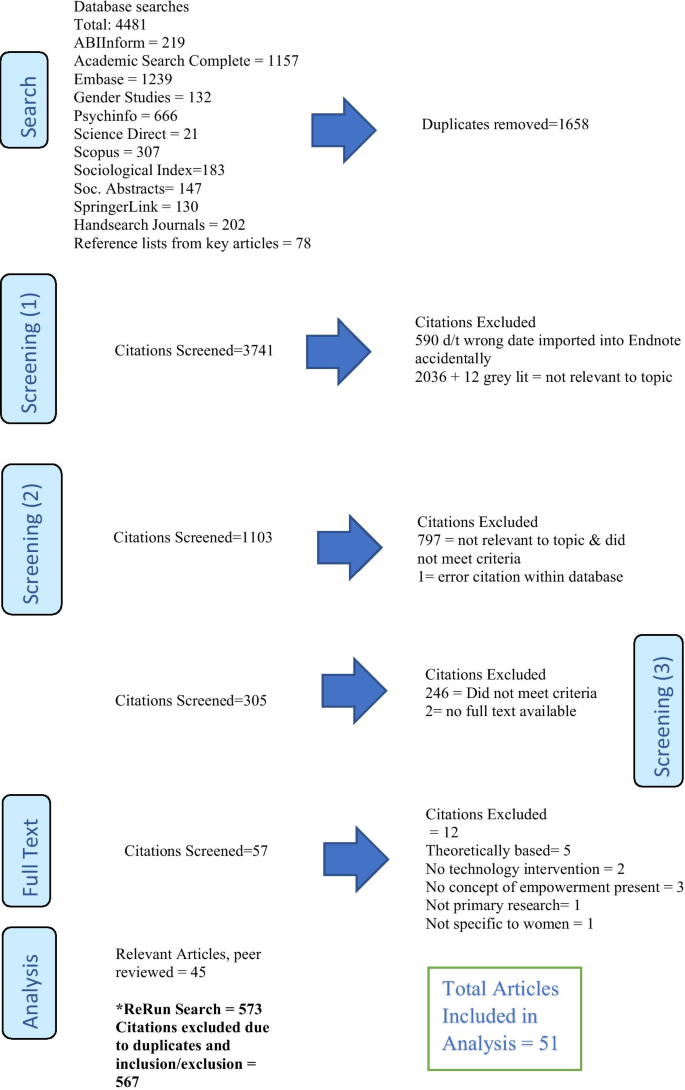
PRISMA Flow for Screening Process
Re-run searches
Due to the extended time to conduct the review, the authors included re-run searches for each database up to January 1, 2018. A total of 573 articles were found in all 10 of the main electronic databases. Using the inclusion and exclusion criteria previously described all but six articles were eliminated through the first and second stages in the review process. The final total number of articles included in the analysis was 51.
Study characteristics, extraction, and charting
The final step in the Arksey and O’Malley’s [ 27 ] scoping review framework was to collate and summarize the results for presentation and discussion. Each selected article was summarized in a customized data characterization utility form to guide data extraction. The goal of this step was to determine and chart factors to be extracted from each article to help answer the research question [ 26 , 27 , 30 ]. The charting of data was an iterative and exploratory process in which the data charts were continuously updated to ensure completeness and accuracy [ 26 , 30 ]. Data extracted from the charts included year of publication, country of study, implications for policy and practice, types of ICT interventions, demographics, empowerment (definition, as a design consideration, and measures), and social determinants of health (presence and description within in the study). All data were then analyzed using thematic analysis and the main ideas refined over several iterations. The data were then mapped using tabular and visual presentations of the main conceptual categories followed by a narrative summary describing how the results related to the research question and objectives.
Demographics and study characteristics
The geographic range of the included evidence was global; however, 41.1% (21/51) described research conducted in the USA. Seven studies were conducted in India, three in Australia, three in Sweden, and two in Canada. One study was conducted in each of the following countries: Finland, Ghana, Italy, Japan, Nepal, Netherlands, Nigeria, Singapore, South Korea, Sri Lanka, Tanzania, Thailand, Uganda, and United Kingdom.
Collation and comparison of demographics was difficult due to a lack of consistency in reporting. However, all articles described the demographics of women who were the primary focus of the study. Seventy eight percent of the articles (40/51) reported on some or all of the descriptive study characteristics. The age of participants was frequently reported although there were inconsistent age groupings across the studies. Some articles only reported the mean age of participants, while others provided only an age range. The lowest mean age reported was 24 years while the highest was 59.6 years; the categories ranged from less than 16 years to 64 years and older. It is difficult to compare these age ranges as the categories varied in the included articles, and it was unclear as to whether age was simply a descriptive statistic designed to describe the sample or whether it was reflected upon consistently in terms of the overall implications to the study.
Missing from the studies were the perspectives and participation of women who could not access, afford, and/or purchase an ICT device as well as effectively and fully utilize it to support their empowerment. Exclusion criteria used in the individual 51 studies illustrate that women not already owning a mobile device, computer, or tablet were eliminated from participating in the research.
Empowerment definition
In the included studies, the concept of empowerment was used incongruously with terms like self-concept, self-esteem, and self-worth, sometimes by the same author in the same study, which further limited our ability to achieve a uniform definition for the purposes of this research. Less than one quarter (12/51) of the studies used the term “empower(ment)” in their definition of the concept of interest. These studies defined empowerment as a process but with different foci: as individuals having choice or control over their decisions [ 31 , 32 , 33 , 34 , 35 , 36 , 37 , 38 ], as being multi-dimensional and influencing a variety of areas [ 34 , 37 , 39 , 40 ] or with a focus on building individuals’ capacities, including internal and external resources [ 39 , 40 , 41 , 42 ].
The remaining studies described empowerment in a more indirect way, never including the term “empower” or “disempower.” Instead, the term empowerment was described in synonymous terms, for instance, half (28/51) described the concept of empowerment as the process of enabling a sense of self-efficacy or self-worth in the ability to overcome barriers to resources, as well as the barriers to decision-making control [ 43 , 44 , 45 , 46 , 47 , 48 , 49 , 50 , 51 , 52 , 53 , 54 , 55 , 56 , 57 , 58 , 59 , 60 , 61 , 62 , 63 , 64 , 65 , 66 , 67 , 68 , 69 , 70 ]. One fifth (11/51) described empowerment as the process enabling a sense of self-efficacy or self-worth in the ability to overcome barriers to control over resources [ 71 , 72 , 73 , 74 , 75 , 76 , 77 , 78 , 79 , 80 , 81 ].
Measures of empowerment
All studies considered the concept of empowerment in their design; 80% (41/51) of the articles considered empowerment as a primary outcome of the study. No measures of empowerment were specifically cited in any of the articles, beyond the measures of the behaviour being studied. Several studies included various measures of self-efficacy (i.e., childbirth [ 74 ], physical activity [ 56 , 67 , 71 , 74 , 80 , 81 ], intimate partner violence [ 72 ], caregiving [ 75 ], barrier [ 55 , 56 ], health [ 78 ], and chronic disease management [ 77 ]). The authors of the articles did not compare the different types of self-efficacy scales for validity of empowerment. The diversity of the scales illustrates a focus on improving efficacy of individual behaviors rather than the holistic empowerment of women.
ICT interventions to support women’s capacity and tools
The articles described a range of supportive ICT interventions, though with inconsistent and overlapping classification. The specific types of interventions covered in the 51 articles included web-based devices (17), the internet (19), particular websites (3), blogs (1), text messaging (4), telemedicine (1), video (1), apps (5), social media (2), computers (6), email (1) and Fitbit™ (1). Our categorization of ICTs focused on how the specific interventions were utilized in the day to day lives of women and were obtained from a thematic analysis of the types of ICTs used by women in the studies. The themes included (1) Outreach; (2) Education; (3) Lifestyle (4) Health Challenges; (5) Prevention; and (6) Perception of Barriers.
Ten of the 51 articles reviewed described supportive ICT interventions as a means of outreach or connecting with clients in the community. Common themes in this section included supporting women where they are at in the community, in terms of their social position, to enhance positive health behaviours with technological assistance, as well as overall enhanced accessibility to ICTs. This was accomplished through Cognitive Behavioural Therapy using computers [ 46 ], and web-based decision aid for understanding fetal anomalies [ 47 ]. Educational text messages were sent to encourage breastfeeding [ 79 ], and general health promotion interventions were delivered as well [ 43 , 44 , 56 , 65 , 73 , 75 , 80 ].
Six articles described supportive ICT interventions that delivered various health information, through smartphones or other web-based devices. These included Facebook™ virtual learning systems [ 34 ], psychoeducation for breast cancer patients [ 35 ], as well as interactive voice response as a tool for improving access to healthcare in remote areas [ 59 ]. Other interventions included English language programs [ 70 ], antenatal perineal massage support groups [ 76 ], as well as support for enhancing doctor-patient relationships. [ 64 ].
Twelve articles described supportive ICT interventions that focused on behavioural outcomes related to general lifestyle areas, using web-based devices. Commonly, the interventions provided some form of external support for women to improve their overall way of being healthy. These included improving nutrition knowledge and behaviours [ 67 , 69 ], promoting healthy food planning, shopping, and eating behaviours [ 54 ], interventions for weight loss behaviours, [ 45 ] and engagement with physical activity coaching [ 55 , 71 , 74 ]. Many of the interventions focused on social networks [ 9 , 48 ], for example, peer support for building social capital [ 52 ], and promoting social behaviours through an iPad book club [ 81 ].
Health challenges
Eleven articles described ICT interventions that focused on using web-based devices to address specific health challenges. The health challenges largely focusing on ways to enhance maintenance of women’s health, for example, self-paced education programs for those who experience intimate partner, as well as dating violence [ 33 , 41 , 72 ], and educational training to enhance understanding and management of chronic illness [ 77 ]. The interventions addressing health challenges were concentrated on those that affect women only, for example educational training for patients with breast cancer [ 38 , 61 ], health modules for those with breast cancer [ 78 ] and stress incontinence [ 63 ] and advanced care planning for women with ovarian cancer [ 49 ].
A few articles (3/51) described ICT interventions that focused on preventing specific health challenges using web-based devices. One intervention focused on the prevention of sexual and reproductive illness using education information [ 57 ]. Another encouraged vaccination behaviors and immunization with educational information [ 58 ] as well as the prevention of pre-eclampsia in rural developing countries using diagnostic tools [ 51 ]. One study focused on utilizing mobile phones to manage money transfers to support transport of women with fistula to urban hospitals [ 60 ] and another examined electronic health records to improve breast cancer screening [ 53 ].
Perceptions of barriers
Nine articles described ICT interventions that focused on the perception of barriers to ICTs that assist women in advancing their understanding and use of ICTs. These studies focused on the perceived barriers and understanding of the role of mobile phones, [ 42 , 66 ] the awareness of gender-based barriers in telemedicine [ 68 ], the development of women through mobile phones [ 32 , 40 ], as well as the connection with women in the community apps [ 50 ].
Concept of empowerment
Empowerment is a multi-dimensional and contextual concept that is internal by nature, varies in meaning, and reflects how women self-ascribe it to themselves. From the outset of the review, search terms had to include words beyond simply “empower[ment]” as much of the initial searching revealed synonyms including self-efficacy, self-worth, self-concept, and/or capacity. This inconsistency in the use of the term empowerment yields a lack of consensus on how empowerment is understood which impacts how research studies and interventions are structured and delivered to ensure maximum effectiveness and generalizability. While none of the studies included in the review indicated the broader negative outcomes related to the use of ICT, the literature supports a flip side to using technology to empower women. For example, technological advances are disproportionately accompanied by female-directed cyber abuse [ 82 , 83 ].
Evidence that women of poor socio-economic status are being left out of research studies and programs that aim to support women’s empowerment, highlights that targeted access and funding for at risk populations (such as sub-populations of women) are essential considerations in policy and program development across individual, community, and global contexts. This also reflects biases in terms of the population sub-groups in research studies that aim to advance empowerment. Opportunities exist for further evaluation of how empowerment is being measured and used in conjunction with ICTs, as well as which frameworks are being used to guide research in this area. The lack of specific measures of empowerment reflects a barrier, not only regarding how strategies for empowerment are understood and implemented, but how researchers know whether empowerment has been achieved. The finding underscores a need for a standardized tool for measuring the level of women’s empowerment.
ICTs to improve empowerment
Empowerment through ICTs has the potential to cross multiple sectors, both private and public. The complexity of empowerment and ICTs, as they relate to the root issues of inequities, suggests the need for collaborative, multi-sectoral involvement. These partnerships consider the contextual factors that act as facilitators and barriers for women in all types of communities. Interagency partnerships are uniquely suited to develop interventions aimed at enabling women to make better use of ICTs. These interventions should include information on access to education, facilities for education regarding entrepreneurship, employment opportunities, and health and other government health resources. Governments partnering with private telecommunication agencies through subsidization could provide discounted or refurbished devices for women who are deemed disadvantaged. Funding may also benefit those who experience difficulty in obtaining mobile devices as well as in accessing interventions aimed at enhancing the use of ICT. For example, funding is needed to support the cost of accessing services, low-cost devices, or the provision of Subscriber Identity Module (SIM) cards. Alternatively, governments should support and encourage private mobile operators through tax exemptions and other benefits to facilitate better mobile services and infrastructure in rural, remote, and urban areas. Providing accessible computer sites within communities or in schools is another way to bridge the gap in access to and use of ICT. These strategies not only help in improving the overall status of girls and women but also influence overall empowerment and development of the community.
Though ICT is not the only factor that can support women’s empowerment through capacity building, women who do not have access to or who cannot afford ICTs, are potentially disempowered due to a lack of voice and participation within the information sphere. Exclusion of such women from research limits the measurement of the true impact of ICTs on empowerment and generalizability of findings. Continued research regarding empowerment involving more advantaged sub-groups of women does not address the inherent issues of oppression of women within society and further disempowers those under-represented groups. Local policies (such as affordable internet as a basic need; basic digital literacy education embedded in local curricula) have the greatest potential of improving the uptake of ICTs, as this process occurs initially at the individual level.
Individual, community, and global knowledge
Local and national governments need to invest in information gathering tools that inquire how and why women are using technology to support their lives and families. Equally important is the inquiry of women’s perceptions regarding how they prefer to use ICTs to improve their lives or the barriers they experience in the process. A global survey undertaken by the UN Statistics Division in 2011 indicated that only 30 percent of countries regularly produce sex-disaggregated statistics (such as male:female access to ICT; digital literacy by gender) and existing data collection approaches do not incorporate qualitative components that highlight the voices of women [ 84 ].
Future data should be translated into gender sensitive policies that support equal access and use of ICTs. The development and implementation of such policies should involve representation of women from all socio-economic backgrounds and ages to ensure maximum impact. Examples include policies that allow women to effectively access and participate in ICTs within society, the delivery of ICTs at a reasonable cost for all, as well as policies that regulate the cost and provision of services linked to ICTs such as availability of cell phone, easily accessible WiFi sites, and cost-effective internet plans.
Limitations
While scoping reviews examine the breadth of evidence available on a topic, they do not factor in the depth or quality of that evidence [ 25 , 26 , 27 , 30 ]. Some authors have argued that scoping reviews should include an assessment of quality; however, Armstrong et al. [ 25 ] contend that this decision should depend on the resources available for the review as well as the purpose of the scoping review itself. The quantity of data that is generated in a scoping review can be significant and so it is important to find a balance between providing an overview of all types of evidence found and providing detailed data and assessment of a smaller number of studies [ 25 ]. Scoping studies also lack a thorough evaluation of the quality of results, instead producing a narrative account of all available evidence [ 26 , 27 ]. This approach serves to ensure that all resulting evidence is included in the review and does not limit the end number of articles, as in a systematic review.
Conclusions
The diversity of technological interventions utilized to support empowerment is infinite and there is no limit to how ICTs can be implemented in daily lives. This study is novel and essential as it comprehensively describes efforts to use ICTs to empower women, and the imperative for collaborations between researchers, program implementers and policy makers to address the persistent gender disparities in the access to and use of technologies. This research provides a foundation for future research on the concept of empowerment with ICTs in critical areas of outreach, education, lifestyle, health challenge, prevention, and perception of barriers. Outreach was linked to positive health behaviours such as health promotion and decision-making applications. Education interventions varied from learning systems to health relationships for knowledge sharing. Lifestyle ICT interventions were related to external supports, often peer based, for improving healthful choices such as coaching and planning tools. Health challenges and prevention were relevant to specific challenges (e.g., intimate partner violence; chronic diseases) and health literacy issues (e.g., vaccine awareness; screening programs), respectively. The final theme of perceptions of barriers reflected experiences by participants respecting uptake, utilization, and ubiquity of ICTs. Each of these areas is well situated for future intervention research and each area brings focal points and imperatives to this emerging research agenda.
Availability of data and materials
The databases used in the study were all open access and included Scopus, Embase, ABI Inform, Soc Index, Sociological Abstracts, Gender Studies, Springer Link, PsychInfo, Science Direct, and Academic Search Complete. The datasets used and/or analysed during the current study are available from the corresponding author on reasonable request.

Abbreviations
Sustainable Development Goals
Information and communication technology
Information and communications technologies
World Health Organization
United Nations
International Telecommunication Union
Global Positioning System
Subscriber Identity Module
Freire, P. (1970). Pedagogy of the Oppressed. (M. B. Ramos, trans.). New York: Continuum.
Grabe S. An empirical examination of women’s empowerment and transformative change in the context of international development. Am J Community Psychol. 2011;49:233–45.
Article Google Scholar
Kabeer N. Resources, agency, achievements: reflections on the measurement of women’s empowerment. Dev Change. 1999;30(43):435–64.
Mosedale S. Assessing women’s empowerment: towards a conceptual framework. J Int Dev. 2005;17:243–57.
Lips H. The gender pay gap: Challenging the rationalizations. Perceived equity, discrimination, and the limits of human capital models. Feminist Forum, 2013;68:169–185. https://doi.org/10.1007/s11199-012-0165-z
Marmot M, Allen J, Bell R, Bloomer E, Goldblatt P. WHO European review of social determinants of health and the health divide. The Lancet. 2012;380(9846):1011–29. https://doi.org/10.1016/S0140-6736(12)61228-8 .
Raphael D. (2012). Tackling Health Inequalities: Lessons from International Experiences . Toronto: Canadian Scholars' Press; 2012.
Statistics Canada. Economic well-being. 2015a. http://www.statcan.gc.ca/pub/89-503-x/2010001/article/11388-eng.htm#a4
Mikkonen J, Raphael D. Social determinants of health: Canadian facts. 2010. http://www.nsgamingfoundation.org/articlesReports/Report_Social_Determinants _of_Health_The_Canadian_Facts.pdf
Public Health Agency of Canada. What determines health? In: Population Health. http://www.phac-aspc.gc.ca/ph-sp/determinants/index-eng.php
United Nations. Sustainable Development Goals Report. https://sustainabledevelopment.un.org/content/documents/21252030%20Agenda%20for%20Sustainable%20Development%20web.pdf
Dixon LJ, Coorea T, Straubhaar J, Covarrubias L, Graber D, Spence J, Rojas V. Gendered spaces: the digital divide between male and female users in internet public access sites. J Comput Med Commun. 2014;19(4):991–1009.
Fang ML, Canham SL, Battersby L, Sixsmith J, Wada M, Sixsmith A. Exploring privilege in the digital divide: Implications for theory, policy, and practice. The Gerontologist. 2018;59(1):e1–15. https://doi.org/10.1093/geront/gny037 .
Pagán FJB, Martínez JL, Máiquez MCC. Internet use by secondary school students: a digital divide in sustainable societies? Sustainability. 2018;10(10):1–14. https://doi.org/10.3390/su10103703 .
Brimacombe T, Skuse A. Gender, ICTs, and indicators: Measuring inequality and change. Gender Technol Dev. 2013;17(2):131–57.
Gurumurthy, A. (2004). Gender and ICTs: Overview report . Retrieved from http://www.bridge.ids.ac.uk/sites/bridge.ids.ac.uk/files/reports/CEP-ICTs-OR.pdf
Intel. (2013). Women and web. Retrieved from http://www.intel.com/content/dam/www/public/us/ en/documents/pdf/women-and-the-web.pdf
Hilbert M. Digital gender divide or technologically empowered women in developing countries? A typical case of lies, damned lies, and statistics. Women’s Stud Int Forum. 2011;34(6):479–89. https://doi.org/10.1016/j.wsif.2011.07.001 .
International Telecommunication Union. ICT facts and figures: 2017. 2017. https://www.itu.int/en/ITU-D/Statistics/pages/facts/default.aspx
Ono H, Zavodny M. Gender and the internet. Soc Sci Quart. 2009;84(1):111–21.
Wasserman IM, Richmond-Abbott MR. Gender and the internet: Causes of variation in access, level, and scope of use. Soc Sci Quart. 2005;86(1):252–70.
Gill, K., Brooks, K., McDougall, J., Patel, P., & Kes, A. (2010). Bridging the gender divide: How technology can advance women economically. Retrieved from http://www.icrw.org/files/publications/Bridging-the-Gender-Divide-How-Technology-can-Advance-Women-Economically.pdf
Gurumurthy, A. (2006). Promoting gender equality? Some development-related uses of ICTs by women. Development in Practice, 16 (6).
Weiss M, Tarchinskaya E. The role of information technologies in changing the status of women to improve human conditions. In: Brocke JV, Stein A, Hofmann S, Tumbas S, editors. Grand societal challenges in information systems research and education. New York: Springer; 2015. p. 51–60.
Chapter Google Scholar
Armstrong R, Hall BJ, Doyle J, Waters E. Scoping the scope of a Cochrane review. J Public Health. 2011;33(1):147–50.
The Joanna Briggs Institute. Methodology for JBI scoping reviews. 2015. http://joannabriggs.org/assets/docs/sumari/Reviewers-Manual_Methodology-for-JBI-Scoping-Reviews_2015_v2.pdf
Arksey H, O’Malley L. Scoping studies: towards a methodological framework. Int J Soc Res Methodol. 2005;8(1):19–32. https://doi.org/10.1080/1364557032000119616 .
Grimshaw J. A guide to knowledge synthesis. Canadian Institutes of Health Research. 2010. http://www.cihr-irsc.gc.ca/e/41382.html
Landa AH, Szabo I, Le Brun L, Owen I, Fletcher G, & Hill M. An evidence-based approach to scoping reviews. The Electronic Journal of Information Systems Evaluation. 2011;10:4: 173–175. http://martinhill.me.uk/pubs/EvidenceBasedApproachToLitReview.pdf
Levac D, Colquhoun H, O’Brien KK. Scoping studies: Advancing the methodology. Implementation Science. 2010;5:1:1–9.
Chew HE, Ilavarasan VP, Levy MR. Mattering matters: agency, empowerment, and mobile phone use by female microentrepreneurs. Inf Technol Dev. 2015;21(4):523–42.
Handapangoda WS, & Sisira Kumara A. From silence to voice: Examining the empowerment potential of mobile phones to women in Sri Lanka: The case of dependent housewives. 2012. https://mpra.ub.uni-muenchen.de/41768/
Lindsay M, Messing JT, Thaller J, Baldwin A, Clough A, Bloom T, ... & Glass N. Survivor feedback on a safety decision aid smartphone application for college-age women in abusive relationships. Journal of Technology in Human Services. 2013;31:4:368–388.
Vivakaran MV, Maraimalai N. Feminist pedagogy and social media: a study on their integration and effectiveness in training budding women entrepreneurs. Gend Educ. 2017;29(7):869–89.
Admiraal JM, van der Velden AW, Geerling J, Burgerhof JG, Bouma G, Walenkamp AM, ... & Reyners AK. Web-based tailored psychoeducation for breast cancer patients at the onset of the survivorship phase: A multicenter randomized controlled trial. Journal of Pain and Symptom Management. 2017;54:4:466–75.
Nord JH, Riggio MT, Paliszkiewicz J. Social and economic development through information and communications technologies: Italy. J Comput Inf Syst. 2017;57(3):278–85.
Google Scholar
Sarkar S. Beyond the “digital divide”: the “computer girls” of Seelampur. Feminist Media Stud. 2016;16(6):968–83.
Siekkinen M, Kesänen J, Vahlberg T, Pyrhönen S, Leino-Kilpi H. Randomized, controlled trial of the effect of e-feedback on knowledge about radiotherapy of breast cancer patients in Finland. Nursing Health Sci. 2015;17(1):97–104.
Holbrey S, Coulson NS. A qualitative investigation of the impact of peer to peer online support for women living with polycystic ovary syndrome. BMC Women’s Health. 2013;13(1):51.
Article PubMed PubMed Central Google Scholar
Islam MK, & Slack F. Women in rural Bangladesh: Empowered by access to mobile phones. In Proceedings of the 9th International Conference on Theory and Practice of Electronic Governance. 2016;March:75–84.
Choo E, Guthrie KM, Mello M, Wetle TF, Ranney M, Tapé C, Zlotnick C. “I need to hear from women who have ‘been there’”: Developing a woman-focused intervention for drug use and partner violence in the emergency department. Partner Abuse. 2016;7(2):193.
Mehta BS, Mehta N. ICT and Socio-economic empowerment of rural women: case of mobile phone in India. Knowl Horizons-Econ. 2014;6(4):103–12.
Brown S, Hudson DB, Campbell-Grossman C, & Yates BC. Health promotion text blasts for minority adolescent mothers. MCN: The American Journal of Maternal/Child Nursing. 2014;39:6:357–362.
Gold KJ, Normandin MM, Boggs ME. Are participants in face-to-face and internet support groups the same? Comparison of demographics and depression levels among women bereaved by stillbirth. Arch Women’s Mental Health. 2016;19(6):1073–8.
Hearn L, Miller M, Lester L. Reaching perinatal women online: The healthy you, healthy baby website and app. J Obesity. 2014;2014:1–9.
Kim DR, Hantsoo L, Thase ME, Sammel M, Epperson CN. Computer-assisted cognitive behavioral therapy for pregnant women with major depressive disorder. J Women’s Health. 2014;23(10):842–8.
Åhman A, Sarkadi A, Lindgren P, Rubertsson C. “It made you think twice”–an interview study of women’s perception of a web-based decision aid concerning screening and diagnostic testing for fetal anomalies. BMC Pregn Childbirth. 2016;16(1):267.
Chib A, Malik S, Aricat RG, Kadir SZ. Migrant mothering and mobile phones: Negotiations of transnational identity. Mobile Media Commun. 2014;2(1):73–93.
Vogel RI, Petzel SV, Cragg J, McClellan M, Chan D, Dickson E, Geller MA. Development and pilot of an advance care planning website for women with ovarian cancer: a randomized controlled trial. Gynecol Oncol. 2013;131(2):430–6.
Ayiasi RM, Kolsteren P, Batwala V, Criel B, & Orach CG. Effect of village health team home visits and mobile phone consultations on maternal and newborn care practices in Masindi and Kiryandongo, Uganda: A community-intervention trial. PloS One.
Jonas SM, Deserno TM, Buhimschi CS, Makin J, Choma MA, Buhimschi IA. Smartphone-based diagnostic for preeclampsia: a mHealth solution for administering the Congo Red Dot (CRD) test in settings with limited resources. J Am Med Inform Assoc. 2015;23(1):166–73.
Wollersheim D, Koh L, Walker R, Liamputtong P. Constant connections: piloting a mobile phone-based peer support program for Nuer (southern Sudanese) women. Aust J Primary Health. 2013;19(1):7–13.
Atlas SJ, Ashburner JM, Chang Y, Lester WT, Barry M, Grant RW. Population-based breast cancer screening in a primary care network. Am J Managed Care. 2012;18(12):821.
Ball K, Mouchacca J, Jackson M. The feasibility and appeal of mobile ‘apps’ for supporting healthy food purchasing and consumption among socioeconomically disadvantaged women: a pilot study. Health Promotion J Aust. 2014;25(2):79–82.
Choi J, hyeon Lee J, Vittinghoff E, & Fukuoka Y. mHealth physical activity intervention: A randomized pilot study in physically inactive pregnant women. Maternal and Child Health Journal. 2016;20:5:1091–1101.
Fjeldsoe BS, Miller YD, Marshall AL. Social cognitive mediators of the effect of the MobileMums intervention on physical activity. Health Psychol. 2013;32(7):729.
Article PubMed Google Scholar
Akinfaderin-Agarau F, Chirtau M, Ekponimo S, Power S. Opportunities and limitations for using new media and mobile phones to expand access to sexual and reproductive health information and services for adolescent girls and young women in six Nigerian states. Afr J Reprod Health. 2012;16(2):219–30.
PubMed Google Scholar
Atkinson KM, Westeinde J, Ducharme R, Wilson SE, Deeks SL, Crowcroft N, Wilson K. Can mobile technologies improve on-time vaccination? A study piloting maternal use of ImmunizeCA, a Pan-Canadian immunization app. Human Vac Immunotherap. 2016;12(10):2654–61.
Brinkel J, May J, Krumkamp R, Lamshöft M, Kreuels B, Owusu-Dabo E, ... & Fobil JN. Mobile phone-based interactive voice response as a tool for improving access to healthcare in remote areas in Ghana: an evaluation of user experiences. Trop Med Int Health 2017;22:5:622–630.
Fiander A, Ndahani C, Mmuya K, Vanneste T. Results from 2011 for the transportMYpatient program for overcoming transport costs among women seeking treatment for obstetric fistula in Tanzania. Int J Gynecol Obstetr. 2013;120(3):292–5.
Kukafka R, Yi H, Xiao T, Thomas P, Aguirre A, Smalletz C, ... & Crew K. Why breast cancer risk by the numbers is not enough: Evaluation of a decision aid in multi-ethnic, low-numerate women. J Med Internet Res. 2015;17:7.
Potnis D. Culture’s consequences: Economic barriers to owning mobile phones experienced by women in India. Telematics Inform. 2016;33(2):356–69.
Sjöström M, Umefjord G, Stenlund H, Carlbring P, Andersson G, Samuelsson E. Internet-based treatment of stress urinary incontinence: a randomised controlled study with focus on pelvic floor muscle training. BJU Int. 2013;112(3):362–72.
Song FW, West JE, Lundy L, Smith DN. Women, pregnancy and health information online: the making of informed patients and ideal mothers. Gender Soc. 2012;26(5):773–98.
Wen KY, Miller SM, Kilby L, Fleisher L, Belton TD, Roy G, Hernandez E. Preventing postpartum smoking relapse among inner city women: development of a theory-based and evidence-guided text messaging intervention. JMIR Res Protocols. 2014;3:2.
Frizzo-Barker J, Chow-White PA. “There’s an App for That” Mediating mobile moms and connected careerists through smartphones and networked individualism. Feminist Media Stud. 2012;12(4):580–9.
Kim C, Draska M, Hess ML, Wilson EJ, Richardson CR. A web-based pedometer programme in women with a recent history of gestational diabetes. Diabet Med. 2012;29(2):278–83.
Article CAS PubMed PubMed Central Google Scholar
Parajuli R, Doneys P. Exploring the role of telemedicine in improving access to healthcare services by women and girls in rural Nepal. Telematics Inform. 2017;34(7):1166–76.
Bissonnette-Maheux V, Provencher V, Lapointe A, Dugrenier M, Dumas AA, Pluye P, Desroches S. Exploring women’s beliefs and perceptions about healthy eating blogs: a qualitative study. J Med Internet Res. 2015;17:4.
Tyers AA Gender Digital Divide? Women learning english through ICTs in Bangladesh. In mLearn. 2012;94–100.
Albright CL, Steffen AD, Novotny R, Nigg CR, Wilkens LR, Saiki K, Brown WJ. Baseline results from Hawaii’s Nā Mikimiki project: a physical activity intervention tailored to multiethnic postpartum women. Women Health. 2012;52(3):265–91.
Gilbert L, Shaw SA, Goddard-Eckrich D, Chang M, Rowe J, McCrimmon T, Epperson M. Project WINGS (Women Initiating New Goals of Safety): A randomised controlled trial of a screening, brief intervention and referral to treatment (SBIRT) service to identify and address intimate partner violence victimisation among substance-using women receiving community supervision. Criminal Behav Mental Health. 2015;25(4):314–29.
Min YH, Lee JW, Shin YW, Jo MW, Sohn G, Lee JH, ... & Yu JH. Daily collection of self-reporting sleep disturbance data via a smartphone app in breast cancer patients receiving chemotherapy: A feasibility study. Journal of Medical Internet Research. 2014;16:5:e135.
Sriramatr S, Berry TR, Spence JC. An Internet-based intervention for promoting and maintaining physical activity: A randomized controlled trial. Am J Health Behav. 2014;38(3):430–9.
Steffen AM, Gant JR. A telehealth behavioral coaching intervention for neurocognitive disorder family carers. Int J Geriatr Psychiatry. 2016;31(2):195–203.
Takeuchi S, Horiuchi S. Randomised controlled trial using smartphone website vs leaflet to support antenatal perineal massage practice for pregnant women. Women and Birth. 2016;29(5):430–5.
Weinert C, Cudney S, Comstock B, Bansal A. Computer intervention: Illness self-management/quality of life of rural women. Can J Nurs Res. 2014;46(1):26–43.
Ventura F, Sawatzky R, Öhlén J, Karlsson P, Koinberg I. Challenges of evaluating a computer-based educational programme for women diagnosed with early-stage breast cancer: a randomised controlled trial. Eur J Cancer Care. 2017;26:5.
Martinez-Brockman JL, Shebl FM, Harari N, Perez-Escamilla R. An assessment of the social cognitive predictors of exclusive breastfeeding behavior using the Health Action Process Approach. Soc Sci Med. 2017;182:106–16.
Article CAS PubMed Google Scholar
Kim HK, Niederdeppe J, Graham M, Olson C, Gay G. Effects of online self-regulation activities on physical activity among pregnant and early postpartum women. J Health Commun. 2015;20:101115–24.
Ehlers DK, Huberty JL, de Vreede GJ. Can an evidence-based book club intervention delivered via a tablet computer improve physical activity in middle-aged women? Telemed e-Health. 2015;21(2):125–31.
Dimond JP, Fiesler C, Bruckman AS. Domestic violence and information communication technologies. Interact Comput. 2011;23(5):413–21. https://doi.org/10.1016/j.intcom.2011.04.006 .
Henry N, Powell A. Technology-facilitated sexual violence: a literature review of empirical research. Trauma Violence Abuse. 2018;19(2):195–208. https://doi.org/10.1177/1524838016650189 .
United Nations Statistics Division. Gender data: Sources, gaps, and measurement opportunities. 2017. http://www.data4sdgs.org/sites/default/files/2017-09/Gender%20Data%20-%20Data4SDGs%20Toolbox%20Module.pdf
Download references
Acknowledgements
Not applicable.
Author information
Authors and affiliations.
University of Saskatchewan, 100-4400 4th Ave, Regina, SK, S4T 0H8, Canada
April Mackey & Pammla Petrucka
You can also search for this author in PubMed Google Scholar
Contributions
AM was involved in the conceptualization, analysis, and writing of the first draft of the manuscript, as well as all edits. PP assisted in analyzing and interpreting the data and was a major contributor in writing the manuscript. All authors read and approved the final manuscript.
Corresponding author
Correspondence to April Mackey .
Ethics declarations
Ethics approval and consent to participate.
Approval from the University of Saskatchewan Behavioural Research Ethics Board was waived for this study as the information retrieved was publicly available.
Consent for publication
Competing interests.
The authors declare that they have no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ . The Creative Commons Public Domain Dedication waiver ( http://creativecommons.org/publicdomain/zero/1.0/ ) applies to the data made available in this article, unless otherwise stated in a credit line to the data.
Reprints and permissions
About this article
Cite this article.
Mackey, A., Petrucka, P. Technology as the key to women’s empowerment: a scoping review. BMC Women's Health 21 , 78 (2021). https://doi.org/10.1186/s12905-021-01225-4
Download citation
Received : 04 December 2019
Accepted : 16 February 2021
Published : 23 February 2021
DOI : https://doi.org/10.1186/s12905-021-01225-4
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Information and communications technology
- Women empowerment
- Scoping review
BMC Women's Health
ISSN: 1472-6874
- General enquiries: [email protected]
What is Empowerment Technology All About?

Empowerment technology is a term that has been gaining popularity in recent years, especially in the context of women’s empowerment. It refers to the use of technology to empower individuals and communities to improve their social, economic, and political status. In essence, it is about using technology as a tool for social change, to break down barriers and provide opportunities for those who have been marginalized or excluded from mainstream society. In this essay, we will explore the concept of empowerment technology, its different forms, and how it can be used to promote female empowerment.
The Meaning of Empowerment Technology
Empowerment technology encompasses a wide range of tools and applications that can be used to promote social, economic, and political empowerment. These tools can include anything from mobile apps and social media platforms to e-learning platforms and online marketplaces. The key feature of empowerment technology is that it is designed to provide individuals with the knowledge, skills, and resources they need to improve their lives and their communities.
Examples of Empowerment Technology
One example of empowerment technology is the use of mobile apps to provide women with information and resources to help them deal with issues such as gender-based violence, reproductive health, and financial literacy. For example, the app “Safecity” allows women to report incidents of harassment and violence in public spaces, providing them with a platform to share their experiences and raise awareness of these issues.
Another example is the use of e-learning platforms to provide women with access to education and training. Online courses, such as those offered by Coursera and Khan Academy, can help women to gain new skills and knowledge in fields such as technology, business, and finance. This can help them to secure better-paying jobs and improve their economic status.
The Benefits of Empowerment Technology
Empowerment technology can have a range of benefits for individuals and communities, including:
- Increased access to information and resources
- Improved social and economic opportunities
- Greater political participation and representation
- Enhanced safety and security
Empowerment technology can also help to break down social barriers and promote greater gender equality. By providing women with the tools and resources they need to succeed, it can help to create a more level playing field and reduce the gender gap in areas such as education, employment, and entrepreneurship.
The Challenges of Empowerment Technology
Despite its many benefits, empowerment technology also faces a number of challenges. One of the biggest challenges is the digital divide, which refers to the gap between those who have access to technology and those who do not. This divide is particularly pronounced in developing countries, where access to technology is often limited, especially for women and girls.
Another challenge is the lack of digital skills and literacy among certain groups, which can limit their ability to take advantage of empowerment technology. This highlights the need for training and education programs that can help to bridge the digital divide and provide individuals with the skills they need to use technology effectively.
Empowerment technology is a powerful tool that can be used to promote social, economic, and political empowerment, especially for women. By providing individuals with access to information, resources, and training, it can help to break down barriers and create opportunities for those who have been marginalized or excluded from mainstream society. However, there are also challenges that need to be addressed, such as the digital divide and the need for digital literacy programs. Overall, empowerment technology has the potential to be a transformative force for good, but it must be used in a way that is inclusive, equitable, and accessible to all.
Personal Finance for Gen Z: Understanding Money Management for the Next Generation
What’s a Synonym for Motherhood?
© 2024 FemiLead


Empowerment Technology
Empowerment Technologies LESSONS 1-15
Lesson 1: introduction to ict.

ICT – Information and Communication-
- It deals with the use of different communication technologies such as mobile phones, telephone, Internet to locate, save, send and edit information
- Is a study of computers as data processing tools. It introduces students to the fundamental of using computer systems in an internet environment.
ICT in the Philippines
- Philippines is dub as the ‘’ICT Hub of Asia” because of huge growth of ICT-related jobs, one of which is BPO, Business Process Outsourcing, or call centers.
- ICT Department in the Philippines is responsible for the planning, development and promotion of the country’s information and communications technology (ICT) agenda in support of national development.

- Means of connecting a computer to any other computer anywhere in the world via dedicated routers and servers.
- Sometimes called simply ‘’the Net’’, is a worldwide system of computer networks- a network of networks in which the users at any one computer can get information from any other computer.

- An information system on the internet that allows documents to be connected to other documents by hypertext links, enabling the user to search for information by moving from one document to another.
- Is an information space where documents and other web resources are identified by URLs, interlinked by hypertext links, and can be accessed via the Internet.
- Invented by Tim-Berners Lee
- Web page is a hypertext document connected to the World Wide Web. It is a document that is suitable for the World Wide Web.
The different online platforms of World Wide Web:
- Web 1.0 – refers to the first stage in the World Wide Web, which was entirely made up of the Web pages connected by hyperlinks.
- Web 2.0 – is the evolution of Web 1.0 by adding dynamic pages. The user is able to see a website differently than others.
– Allows users to interact with the page; instead of just reading the page, the user may be able to comment or create user account.
- Web 3.0 – this platform is all about semantic web.
– Aims to have machines (or servers) understand the user’s preferences to be able to deliver web content.
Static Web Page- is known as a flat page or stationary age in the sense that the page is ‘’as is’’ and cannot be manipulated by the user. The content is also the same for all users that is referred to as Web 1.0
Dynamic Web Pages – web 2.0 is the evolution of web 1.0 by adding dynamic web pages. The user is able to see website differently than others e.g. social networking sites, wikis, video sharing sites.
FEATURES OF WEB 2.0
- Folksonomy- allows user to categorize and classify information using freely chosen keywords e.g. tagging by FB, Twitter, use tags that start with the sign #, referred to as hashtag.
- Rich User Experience – content is dynamic and is responsive to user’s input
- User Participation- The owner of the website is not the only one who is able to put content. Others are able to place a content of their own by means of comments, reviews and evaluation e.g. Lazada, Amazon.
- Long Tail – services that are offered on demand rather than on a one-time purchase. This is synonymous to subscribing to a data plan that charges you for the amount of time you spent in the internet.
- Software as a services- users will be subscribe to a software only when needed rather than purchasing them e.g. Google docs used to create and edit word processing and spread sheet.
- Mass Participation – diverse information sharing through universal web access. Web 2.0’s content is based on people from various cultures.

Six types of Social Media :
a) Social Networks – These are sites that allows you to connect with other people with the same interests or background. Once the user creates his/her account, he/she can set up a profile, add people, share content, etc
Example: Facebook and Google+

b) Bookmarking Sites – Sites that allow you to store and manage links to various website and resources. Most of the sites allow you to create a tag to others.
Stumble Upon, Pinterest
Ex. Reddit and Digg

d) Media Sharing – sites that allow you to upload and share media content like images, music and video.

- iOS – use in apple devices such as iPhone and iPad
- Android – an open source OS developed by Google. Being open source means mobile phone companies use this OS for free.
- Blackberry OS – use in blackberry devices
- Windows phone OS – A closed source and proprietary operating system developed by Microsoft.
- Symbian – the original smartphone OS. Used by Nokia devices
- WebOS- originally used in smartphone; now in smart TVs.
- Windows Mobile – developed by Microsoft for smartphones and pocket PCs

- e.g. Yahoo!, Gmail, HotmailCloud computing- distributed computing on internet or delivery of computing service over the internet.

-Instead of running an e-mail program on your computer, you log in to a Web
e-mail account remotely. The software and storage for your account doesn’t exist
on your computer – it’s on the service’s computer cloud.
It has three components
- Client computers – clients are the device that the end user interact with cloud.
- Distributed Servers – Often servers are in geographically different places, but server acts as if they are working next to each other.
- Datacenters – It is collection of servers where application is placed and is accessed via Internet.

TYPES OF CLOUDS
PUBLIC CLOUD allows systems and services to be easily accessible to the general public. Public cloud may be less secured because of its openness, e.g. e-mail
PRIVATE CLOUD allows systems and services to be accessible within an organization. It offers increased security because of its private nature.
COMMUNITY CLOUD allows systems and services to be accessible by group of organizations.
HYBRID CLOUD is a mixture of public and private cloud. However, the critical activities are performed using private cloud while the non-critical activities are performed using public cloud.
LESSON 2: ONLINE SAFETY, SECURITY AND RULES OF NETIQUETTE

TEN RULES OF NETIQUETTE
Rule No. 1: Remember the human
- You need to remember that you are talking to a real person when you are online.
- The internet brings people together who would otherwise never meet.
- Remember this saying when sending an email: Would I say this to the person’s face.
Rule No. 2: Adhere to the same standards online that you follow in real life.
- You need to behave the same way online that you do in real life.
- You need to remember that you can get caught doing things you should not be doing online just like you can in real life.
- You are still talking to a real person with feelings even though you can’t see them.
Rule no. 3: Know where you are in cyberspace.
- Always take a look around when you enter a new domain when surfing the web.
- Get a sense of what the discussion group is about before you join it.
Rule no. 4: Respect other people’s time and bandwidth.
- Remember people have other things to do besides read your email. You are not the center of their world.
- Keep your post and emails to minimum by saying what you want to say.
- Remember everyone won’t answer your questions.
Rule no. 5: Make yourself look good online.
- Be polite and pleasant to everyone.
- Always check your spelling and grammar before posting.
- · Know what you are talking about and make sense saying it.
Rule no. 6: Share expert knowledge
- Ask questions online
- Share what you know online.
- Post the answers to your questions online because someone may have the same question you do.
Rule no. 7: Help keep flame wars under control
- Netiquette does not forgive flaming.
- Netiquette does however forbid people who are flaming to hurt discussion groups by putting the group down.
Rule no. 8: Respect other people’s privacy.
- Do not read other people’s mail without their permission.
- Going through other people’s things could cost you, your job or you could even go to jail.
- Not respecting other people’s privacy is a bad netiquette.
Rule no. 9: Don’t abuse your power.
- Do not take advantage of other people just because you have more knowledge or power than them.
- Treat others as you would want them to treat you if the roles were reversed.
Rule no. 10: Be forgiving of other people’s mistake.
- Do not point out mistakes to people online.
- Remember that you were once the new kid on the block.
- You still need to have a good manners even though you are online and cannot see the person face to face.
Internet security
Security Requirement Triad

- Integrity Data integerity System integrity
- Availability
Misuse: Causes a system component to perform a function or service that is detrimental to system security.
Types of System Intruders
- Masquerader
- Hackers
- Clandestine user

Parts of Virus
- Infection mechanism
Virus stages
- Dormant phase Virus is idle.
- Propagation phase Virus places an identical copy of itself into other programs or into certain system areas on t the disk.
- Triggering phase Virus is activated to perform the function for which it was intended. Caused by a variety of system events
- Execution phase Function is performed
Cyber crime- a crime committed or assisted through the use of the Internet.
Privacy Policy/Terms of Services (ToS) – tells the user how the website will handle its data.
Malware- stands for malicious software.
Virus- a malicious program designed to transfer from one computer to another in any means possible.
Worms – a malicious program designed to replicate itself and transfer from one file folder to another and also transfer to other computers.
Trojan -a malicious program designed that is disguised as a useful program but once downloaded or installed, leaves your PC unprotected and allows hacker to get your information.
Spyware – a program that runs in the background without you knowing it. It has the ability to monitor what you are currently doing and typing through key logging.
Adware- a program designed to send you advertisement, mostly pop-ups.
Spam – unwanted email mostly from bots or advertisers.
Phishing- acquires sensitive personal information like passwords and credits card details.
Pharming- a more complicated way of phishing where it exploits the DNS system.
Copyright- a part of law, wherein you have the rights to work, anyone who uses it w/o your consent is punishable by law.
Fair Use- means that an intellectual property may be used w/o consent as long as it is used in commentaries, criticism, parodies, research and etc.
Keyloggers- used to record the keystrokes done by user. This is done to steal passwords or any other sensitive information.
Rogue security softwares – is a form of malicious software and internet fraud that misleads users into believing there is a virus on their computer, and manipulates them into paying money for a fake malware removal tool.
Four search strategies
- Keyword searching
Enter terms to search
Use quotation marks to search as a phrase and keep the words linked together
Common words are ignored (That, to, which, a, the …)
+ and – can be used to include or exclude a word
- Boolean
AND – enter words connect with AND- it will include sites where both words and found
Uses: joining different topics (i.e. global warming AND California)
OR – requires at least one of the terms is found.
Uses: join similar or synonymous topics (i.e. global warming OR greenhouse effect)
NOT – searches for the first term and excludes sites that have the second term.
(i.e. Washington NOT school)
- Question
a question may be entered in the search field of search engine
- Advanced Features are offered on many engines by going to an “Advanced search” page and making selections. Effective in narrowing search returns to a specific topic or phrase.
LESSON 3: Advanced Word Processing Skills
Lesson Discussion
In the professional world, sending out information to convey important information is vital. Because of ICT, things are now sent much faster than the traditional newsletters or postal mail. You can now send much faster than the traditional newsletters or postal mail. You can now use the Internet to send out information you need to share. What if we could still do things much faster – an automated way of creating and sending uniform letters with different recipients? Would that not be more convenient?
I. Mail Merge and Label Generation
A. Mail Merge
One of the important reasons in using computers per se is its ability to do recurring tasks automatically. But this ability has to be honed by learning the characteristics and features of the software you use with your computer. After all, no matter how good or advance your computer and software may be, it can only be as good as the person using it.
In this particular part of our lesson, we will learn one of the most powerful and commonly used features of Microsoft Word called Mail Merge. As the name suggests, this feature allows you to create documents and combine or merge them with another document or data file. It is commonly used when sending out advertising materials to various recipients.
The simplest solution for the scenario above is to create a document and just copy and paste it several times then just replace the details depending on whom you send it to. But what if you have hundreds or thousands of recipients? Would not that take too many hours? What if you have a small database of information where you can automatically generate those letters?

Two Components of Mail Merge
1. Form Document
The first component of our mail merged document is the form document. It is generally the document that contains the main body of the message we want to convey or send. The main body of the message is the part of the form document that remains the same no matter whom you send it to from among your list.
Also included in the form document is what we call place holders, also referred to as data fields or merge fields. This marks the position on your form document where individual data or information will be inserted. From our sample document, the place holders are denoted or marked by the text with double-headed arrows (<< >>) on each side and with a gray background. On a printed standard form, this will be the underlined spaces that you will see and use as a guide to where you need to write the information that you need to fill out. In its simplest form, a form document is literally a “form” that you fill out with individual information. A common example of a form document is your regular tax form or application form.

2. List or Data File
The second component of our mail merged document is the list or data file. This is where the individual information or data that needs to be plugged in (merged) to the form document is placed and maintained. One of the best things about the mail merge feature is that it allows data file to be created fro within the Microsoft Word application itself, or it gets data from a file created in Microsoft Excel or other data formats. In this way, fields that needed to be filled up on the form document can easily be maintained without accidentally altering the form or main document. You can also easily add, remove, modify, or extract your data more efficiently by using other data management applications like Excel or Access and import them in Word during the mail merge process.

B. Label Generation
Included in the mail merge feature on Microsoft Word is the Label Generator. It just makes sense that after you print out your form letters, you will need to send it to individual recipients in an envelope with the matching address printed directly on the envelope or on a mailing label to stick on. By using virtually the same process as a standard mail merge, Microsoft Word will print individual addresses to a standard form that it has already pre-formatted. Simply put, it creates a blank form document that simulates either a blank label or envelope of pre-defined size and will use the data file that you selected to print the information, typically individual addresses. So even in generating labels, the two essential components of creating a merged document are present: the form document and the data file. Only in this case, you did not have to type or create the form document yourself because it was already created and pre-formatted in Microsoft Word. All you need to do is select the correct or appropriate size for the label or envelope and select the data file that contains the addresses (data) to be printed. You can also preview your merged labels before printing if you want to.

II. Integrating Images and External Materials
Integrating or inserting pictures in your document is fun and it improves the impression of your document. A common use of inserting a picture on a document is when you are creating your resume. Though seemingly simple to do, your knowledge on the different kinds of materials that you can insert or integrate in a Word document and its characteristics can help you create a more efficient, richer document not only in content but also in physical form. A better understanding of the physical form of your document as well as the different materials you would integrate in it would allow you to be more efficient and versatile in using Microsoft Word.
A. Kinds of Materials
There are various kinds of materials Microsoft Word is capable of integrating to make the documents richer, more impressive, and more informative.
1. Pictures
Generally, these are electronic or digital pictures or photographs you have saved in any local storage device. There are three commonly used types of picture files. You can identify them by the extension on their file names.

a. .JPG/JPEG
This is pronounced as “jay-peg“ and is the short form of .jpeg or Joint Photographic Experts Group. Like all the rest of the image file extensions, it identifies the kind of data compression process that it uses to make it more compatible and portable through the Internet. This type of image file can support 16.7 million colors that is why it is suitable for use when working with full color photographic images. Unfortunately, it does not support transparency and therefore, images of this file type can be difficult to integrate in terms of blending with other materials or elements in your document. But if you are looking for the best quality image to integrate with your document then this is the image file type for you. .JPG does not work well on lettering, line drawings, or simple graphics. .JPG images are relatively small in file size.
This stands for Graphics Interchange Format. This type of image file is capable of displaying transparencies. Therefore, it is good for blending with other materials or elements in your document. It is also capable of displaying simple animation. Apparently, this may not be too useful on a printed document but if you are sending documents electronically or through email, or even post documents into a website, then this could be quite impressive. The downside is that it can only support up to 256 colors so it is good mostly on logos and art decors with very limited, and generally solid colors. .GIF is much better for logos, drawings, small text, black and white images, or low-resolution files.
Example of a .gif format picture.
This is pronounced as “ping“. It stands for Portable Network Graphics. It was built around the capabilities of .GIF. Its development was basically for the purpose of transporting images on the Internet at faster rates. It is also good with transparencies but unlike .GIFs, it does not support animation but it can display up to 16 million colors, so image quality for this image file type is also remarkably improved. .PNG allows the control of the transparency level or opacity of images.

Example of .png format picture.
2. Clip Art
This is generally a .GIF type; line art drawings or images used as generic representation for ideas and objects that you might want to integrate in your document. Microsoft Word has a library of clip arts that is built in or can be downloaded and used freely. There are still other clip arts that you can either purchase or freely download and use that come from third-party providers.

Clip Art Icon in Microsoft Office 2010.
These are printable objects or materials that you can integrate in your document to enhance its appearance or allow you to have some tools to use for composing and representing ideas or messages. If you are designing the layout for a poster or other graphic material for advertising, you might find this useful.

Shapes Icon under the Insert ribbon tab.
4. Smart Art
Generally, these are predefined sets of different shapes grouped together to form ideas that are organizational or structural in nature. If you want to graphically represent an organization, process, relationships, or flow for infographic documents, then you will find this easy and handy to use.

Another type of material that you can integrate in your Word document that allows you to represent data characteristics and trends. This is quite useful when you are preparing reports that correlate and present data in a graphical manner. You can create charts that can be integrate in your document either directly in Microsoft Word or imported from external files like Microsoft Excel.

Chart – Used to illustrate and compare data.
6. Screenshot
Sometimes, creating reports or manuals for training or procedures will require the integration of a more realistic image of what you are discussing on your report or manual. Nothing can get you a more realistic image than a screenshot. Microsoft Word even provides a snipping tool for your screen shots so you can select and display only the part that you exactly like to capture on your screen.

III. Image Placement
Layout of text wrapping options.
A. In Line with Text
This is the default setting for images that are inserted or integrated in your document. It treats your image like a text font with the bottom side totally aligned with the text line. This setting is usually used when you need to place your image at the beginning of a paragraph. When placed between texts in a paragraph or a sentence, it distorts the overall appearance and arrangement of the texts in the paragraph because it will take up the space it needs vertically, pushing whole lines of texts upward.
This setting allows the image you inserted to be placed anywhere with the paragraph with the text going around the image in a square pattern like frame.
This is almost the same as the Square setting, but here the text “hug” or conforms to the general shape of the image. This allows you to get a more creative effect on your document. This setting can mostly be achieved if you are using an image that supports transparency like a .GIF or .PNG file.
This setting allows the text on your document to flow even tighter taking the contours and shape of the image. Again, this can be best used with .GIF or .PNG type of image.
E. Top and Bottom
This setting pushes the texts away vertically to the top and/or the bottom of the image so that the image occupies a whole text line on its own.
F. Behind Text
This allows your image to be dragged and placed anywhere on your document but with all the texts floating in front of it. It effectively makes your image look like a background.
G. In Front of Text
As it suggests, this setting allows your image to be placed right on top of the text as if your image was dropped right on it. That means whatever part of the text you placed the image on, it will be covered by the image.
IV. Key Terms
- Mail Merge – a feature that allows you to create documents and combine or merge them with another document or data file.
- Form Document – the document that contains the main body of the message we want to convey or send.
- Data File – includes the individual information or data or the recipient’s information.
- Merge Field/Place Holder – marks the position on your form document where individual data or information will be inserted.
- .JPG – file extension for the Joint Photographic Experts Group picture file.
- .PNG – file extension for Portable Network Graphics image file.
- .GIF – file extension for the Graphics Interchange Format image file.
- Clipart – line art drawings or images used as a generic representation for ideas and objects.
- Smart Art – predefined sets of different shapes grouped together to form ideas that are organizational or structural in nature.
- Text Wrap – adjusts how the image behaves around other objects or text.
LESSON 4: Advanced Spreadsheet Skills
- What is a Spreadsheet Software? • allows users to organize data in rows an columns and perform calculations on the data • These rows and columns collectively are called worksheet.
- 3. Examples of Spreadsheet Software: • LibreOffice Calc • OpenOffice.org Calc • Google Sheets • Apple iWork Numbers • Kingsoft Office Spreadsheets • StarOffice Calc • Microsoft Excel
- 4. MICROSOFT EXCEL
- 5. To open Microsoft Excel, Press “Windows Logo” + R then type “excel” then enter.
- 6. Key Terms in MS Excel: • Row – horizontal line of entries in a table • Column – vertical line of entries in a table • Cell – the place where info. is held in a spreadsheet
- 7. Key Terms in MS Excel: • Active Cell – the selected cell • Column Heading – the box at the top of each column containing a letter • Row Heading – the row number
- 8. Key Terms in MS Excel: • Cell Reference – the cell address of the cell usually combine letter and number (ex. A1, B4, C2) • Merge – combining or joining two or more cells • Formula – is an expression which calculates the value of a cell.
- 9. Key Terms in MS Excel: • Functions – are predefined formulas and are already available in Excel • Formula Bar – the bar that displays the contents of a cell
- 10. FUNCTIONS
- 11. BASIC MATH OPERATIONS: • =SUM(x,y) or =SUM(range) – returns the sum of x and y or (all the numbers within the range) • =PRODUCT(x,y) – returns the product of x and y • =QUOTIENT(x,y) – returns the quotient of x divided by y • =x-y – returns the difference of x subtracted by y
- 12. BASIC MATH OPERATIONS: • =x+y – returns the sum of x and y • =x*y – returns the product of x and y • =x/y – returns the quotient of x divided by y • =x-y – returns the difference of x subtracted by y
- 13. OTHER FUNCTIONS: • =ABS(x) – returns the absolute value of x • =AVERAGE(x,y) – returns the average of x and y • =CONCATENATE(x,y) – joins x and y
- 14. OTHER FUNCTIONS: • =IF(Condition, x, y) – returns x if the condition is true, else it returns y • =ISEVEN(x) – returns true if x is an even number • =ISODD(x) – returns true if x is an odd number
- 15. OTHER FUNCTIONS: • =COUNT(range) – counts the number of cell containing a number within a range • =COUNTIF(range, criteria) – count the number of cell that fits with the criteria within the range
- 16. OTHER FUNCTIONS: • =ISNUMBER(x) – returns true if x is a number • =ISTEXT(x) – returns true if x is a text • =LEN(x) – returns the length of characters in x • =PROPER(x) – returns the proper casing of x
- 17. OTHER FUNCTIONS: • =LEFT(x,y) – returns the characters of x specified by y (from the left) • =RIGHT(x,y) – returns the characters of x specified by y (from the right) • =PI() – returns the value of pi
- 18. OTHER FUNCTIONS: • =MIN(x,y) – returns the smallest number between x and y • =MAX(x,y) – returns the largest number between x and y • =MIN(range) – returns the smallest number within the range • =MAX(range) – returns the largest number within the range
- 19. OTHER FUNCTIONS: • =POWER(x,y) – returns the value of x raised to the power of y • =ROUND(x,y) – rounds x to a specified number of digits (y) =COLUMN(x) – returns the column number of x • =ROW(x) – returns the row number of x
- 20. OTHER FUNCTIONS: • =SQRT(x) – returns the square root of x • =TRIM(x) – removes extra spaces in x • =UPPER(x) – returns x in all capital form • =LOWER(x) – returns x in non- capital form
- 21. OTHER FUNCTIONS: • =TODAY() – returns the current date • =NOW() – returns the current date and time
- 22. EXERCISES
- 23. Consider this data: NAME MATH GRADE SCIENCE GRADE FILIPINO GRADE ENGLISH GRADE A.P GRADE MARK 75 70 78 81 78 PETE 84 87 86 88 85 ANA 91 92 95 90 90 REA 73 75 74 75 70
- 24. Give the formulas to get : • Mark’s , Pete’s, Ana’s and Rea’s averages • The highest grade that Ana got • The lowest grade that Mark got? • Sum of all Math Grade? Science? A.P.? • Sum of all Rea’s Grades • The Lowest Number among all grades • The remarks (Passed or Failed)
- 25. Now, consider this data: FIRST NAME MIDDLE NAME LAST NAME MARK CURTIS WILLIAMS PETE MCCLOEY HARRISON ANA MONROE FRITZ REA TAN COLLINS
- 26. Give the formulas to get : • Mark’s Full Name • Ana’s Full Name in Proper Case • Count the number of letters that Pete’s Last Name has • “COLL” from Rea’s Last Name • “LOEY” from Pete’s Middle Name • Combining “WILL” and “LINS” from Mark and Rea’s Last Names respectively
LESSON 5: Advanced Presentation Skills
Powerpoint is a highly innovative and versatile program that can ensure a successful communication whether you’re presenting in front of potential investors, a lecture theatre or simply in front of your colleagues. The following are the five features you should be using-if youy aren’t already. Learn everything about these tips: they will improve your presentation skills and allow you to communicate your message successfully. The five features of powerpoint was
1)adding smart art
2)Inserting Shapes
3)Inserting and Image
4)Slide Transitions
5)Adding Animations
Creating an Effective Presentation
lesson 6: imaging and design for online environment.

PHOTO EDITING
- Photo editing encompasses the processes of altering images, whether they are digital photographs, traditional photo chemical photographs, or illustrations. Traditional analog image editing is known as photo retouching, using tools such as an airbrush to modify photographs, or editing illustrations with any traditional art medium.

- Which can be broadly grouped into vector graphics editors, raster graphics editors, and 3D modelers are the primary tools with which a user may manipulate, enhance, and transform images. Many image editing programs are also used to render or create computer art from scratch.
BASIC OF IMAGE EDITING
- RASTER IMAGES are stored in a computer in the form of a grid of picture elements or pixels.
- VECTOR IMAGES such as Adobe Illustrator, Inkscape and etc. are used to create and modify vector images, which are stored as descriptions of lines, Bezier curves and text instead of pixels.
DIFFERENCE BETWEEN RASTER AND VECTOR IMAGES

- VECTOR IMAGES alternatively, allow for more flexibility. Constructed using mathematical formulas rather than individual colored blocks, vector file types such as EPS, AI and PDF are excellent for creating graphics that frequently require resizing. 3 . 3D MODELING (OR MODELLING ) is the process of developing a mathematical representation of any three dimensional surface of an object via specialized software. The product is called a 3D model. It can be displayed as a two-dimensional image through a process called 3D rendering or used in a computer simulation or physical phenomena. The model can also be physically created using 3D printing devices.

Ø JPEG is a commonly used method of lossy compression for digital images, particularly for those images produced by a digital photography.
Ø PNG (PORTABLE NETWORK GRAPHICS) is a raster graphics file format that supports lossless data compression.
Ø GIF a lossless format for image files that supports both animated and static images.
Ø BMP is a raster graphics image used to store bitmap digital images
Ø EPS used in vector-based images in Adobe Illustrator.
Ø SVG is an XML-based vector image format for two-dimensional graphics w/ support for interactivity and animation
Ø .3ds is one of the file formats used by the Autodesk 3Ds Max 3D Modelling, animation and rendering software.
Ø .fbx is an exchange format, in particular for interoperability between Autodesk products and other digital content creation software
FEATURES OF IMAGE EDITORS
SELECTION One of the prerequisites for many of the app mentioned below is a method of selecting part(s) of an image, thus applying a change selectively without affecting the entire picture
Ø MARQUEE TOOL for selecting rectangular or other regular polygon-shaped regions
Ø LASSO TOOL for freehand selection of a region
Ø MAGIC WAND TOOL selects objects or regions in the image defined by proximity of color or luminance

CROPPING creates a new image by selecting a desired rectangular portion from the image being cropped. The unwanted part of the image is discarded. Image cropping does not reduce the resolution of the area cropped.

IMAGE ORIENTATION – Image editors are capable of altering an image to be rotated in any direction and to any degree. Mirror images can be created and images can be horizontally flipped or vertically flopped. Rotated image usually require cropping afterwards, in order to remove the resulting gaps at the image edges.

Contrast of images and brighten or darken the image. Underexposed images can be often be improved by using this feature.
Brightening lightens the image so the photo brightens up. Brightness is a relative expression of the intensity of the energy output of a visible light source.
Adjusting contrast means adjusting brightness because they work together to make a better image.

Photo manipulation involves transforming or altering a photograph using various methods and techniques to achieve desired results. Some photo manipulations are considered skillful artwork while others are frowned upon as unethical practices, especially when used to deceive the public, such as hat used for political propaganda , or to make a product or person look better.

DIFFERENCES PHOTO EDITING – signifies the regular process used to enhance photos and to create them ‘’Actual editing simple process’’. Also includes some of the regular programs used for editing and expose how to use them. PHOTO MANIPULATION – includes all simple editing techniques and have some manipulation techniques like erasing, adding objects , adding some graphical effects, background correction, creating incredible effect, change elements in an image, adding styles , eliminating blemishes from a person’s face and changing the features of a person’s body.

b.) Infographics
also known as data visualization, information design, and communication design
- It is any graphic that display and explains information, whether that be data or words. When we use the term ‘’infographics’’, we’re using it as a general term used to describe data presented in a visual way.
- Infographics are important because they change the way people find and experience stories. Infographics are being used to augment editorial content on the web, it create a new way of seeing the world of data, and they help communicate complex ideas in a clear and beautiful way.
TYPES OF INFOGRAPHICS
- Statistical
- Process Flow
PROCESS OF MAKING INFOGRAPHICS
- a)Know what is needed
- b)Take a reference
- c)Know the audience
- d)Decide the type of infographics
- a)Gather ideas
- b)Build thought process
- a) Choose your tool and start designing
- a) Cross check the data to deliver flawless output
- a) Make it viral
- b) Share on social network
BEST PRACTICES WHEN CREATING INFOGRAPHICS
- a)Maintain a structure
- b)Don’t use more than 3 color palletes
- c)Typography matters a lot
- d)Include source and references
LESSON 7: Online Platforms for ICT Content Development
- Marketplace – allows members to post, read and respond to classified ads.
- Groups – allows members who have common interests to find each other and interact.
- Events – allows members to publicize an event, invite guests and track who plans to attend.
- Pages – allows members to create and promote a public page built around a specific topic.
- Presence technology – allows members to see which contacts are online and chat.
Within each member’s personal profile, there are several key networking components. The most popular is arguably the Wall, which is essentially a virtual bulletin board. Messages left on a member’s Wall can be text, video or photos. Another popular component is the virtual Photo Album. Photos can be uploaded from the desktop or directly from a smartphone camera. There is no limitation on quantity, but Facebook staff will remove inappropriate or copyrighted images. An interactive album feature allows the member’s contacts (who are called generically called “friends”) to comment on each other’s photos and identify (tag) people in the photos. Another popular profile component is status updates, a microblogging feature that allows members to broadcast short Twitter-like announcements to their friends. All interactions are published in a news feed, which is distributed in real-time to the member’s friends.
Facebook offers a range of privacy options to its members. A member can make all his communications visible to everyone, he can block specific connections or he can keep all his communications private. Members can choose whether or not to be searchable, decide which parts of their profile are public, decide what not to put in their news feed and determine exactly who can see their posts. For those members who wish to use Facebook to communicate privately, there is a message feature, which closely resembles email.
2. Instagram

Instagram is an online mobile photo-sharing site that allows its users to share pictures and videos either publicly or privately on the app, as well as through a variety of other social networking platforms, such as Facebook , Twitter , Tumblr , and Flickr . Originally, a distinctive feature was that it confined photos to a square shape, similar to Kodak Instamatic and Polaroid SX-70 images, in contrast to the 4:3 aspect ratio typically used by mobile device cameras. In August 2015, version 7.5 was released, allowing users to upload media captured in any aspect ratio. Users can also apply digital filters to their images. Videos on Instagram debuted in June 2013, allowing prerecorded square standard definition resolution clips of up to 15 seconds to be shared; later improvements added support for widescreen resolutions of up to 1080p and longer recording times for either prerecorded (up to one minute) or disappearing live (up to one hour) videos.
Instagram was created by Kevin Systrom and Mike Krieger , and launched in October 2010 as a free mobile app . The service rapidly gained popularity, with over 100 million active users as of April 2012 [10] [11] and over 300 million as of December 2014. [12] Instagram is distributed through the Apple App Store and Google Play . [13] Support for the app is available for iPhone , iPad , iPod Touch , Windows 10 devices and Android handsets, while third-party Instagram apps are available for BlackBerry 10 and Nokia- Symbian Devices.

Twitter is an online news and social networking service where users post and interact with messages, “tweets,” restricted to 140 characters . Registered users can post tweets, but those who are unregistered can only read them. Users access Twitter through its website interface, SMS or a mobile device app . [10] Twitter Inc. is based in San Francisco , California , United States , and has more than 25 offices around the world.
Twitter is about learning and adding value
It is also about adding value to others by giving or sharing something valuable to them so that they are able to learn something. That is why I usually tweet about stuff that I read, learned or have good value. I have learned so much from the others that is why I love twitter. It is also about helping others, I disagree with many ‘experts’ that say you should only follow ‘influential’ users because I don’t judge someone that way, and because I believe the people at Twitter don’t believe in them either. I also disagree that you should only share your own stuff otherwise you will dilute your brand. Sure it makes sense but 24/7 sharing your own blog post and following influential people?
BLOGGING SITES

Weebly is one of the easiest website builders in the market . They allow you to drag and drop content into a website, so it’s very intuitive to use ( click here to see our opinion on Weebly ).
By using Weebly’s website building elements, you can literally drag them into your website and have a website built relatively quickly, and painlessly. The beauty of this system is that you can pretty much drag the elements to wherever you want – so it’s not very restrictive on where and how you place your website content.
Weebly’s elements include pictures, paragraphs, videos, buttons, maps, contact forms – basically all the basics for website building.

Tumblr is a popular microblogging platform designed for creative self-expression. It is considered a mindful alternative to Facebook and other social media websites where users blog on a myriad of topics.
You can link your Tumblr account to other social networks you use and you can feed your traditional blog or other RSS feed to your Tumblelog. You can also create static pages such as your own Questions page that people are automatically taken to when they ask you a question. If you want to make your Tumblelog look more lie a traditional website, you can do it by adding pages. You can make your Tumblelog private or just make specific posts private as needed, and you can schedule posts to publish in the future.
It’s also easy to invite other people to contribute to your Tumblelog.
If you want to track your stats, you can add any analytics tracking code to your Tumblelog. Some users will even burn a feed with Feedburner, create custom themes, and use their own domain names
3. Pinterest

Pinterest is a free website that requires registration to use. Users can upload, save, sort, and manage images—known as pins—and other media content (e.g., videos) through collections known as pinboards. Pinterest acts as a personalized media platform. Users can browse the content of others in their feed. Users can then save individual pins to one of their own boards using the “Pin It” button, with pinboards typically organized by a central topic or theme. Users can personalize their experience by pinning items, creating boards, and interacting with other members. The end result is that the “pin feed” of each user displays unique, personalized results.
Content can also be found outside of Pinterest and similarly uploaded to a board via the “Pin It” button, which can be downloaded to the bookmark bar on a web browser, or be implemented by a webmaster directly on the website. They also have the option of sending a pin to other Pinterest users and email accounts through the “Send” button. Some websites include red and white “pin it” buttons on items, which allow Pinterest users to pin them directly.
Initially, there were several ways to register a new Pinterest account. Potential users could either receive an invitation from an already registered friend, or they could request an invitation directly from the Pinterest website that could take some time to receive. An account can also be created and accessed by linking Pinterest to a Facebook or Twitter profile. When a user re-posts or re-pins an image to their own board, they have the option of notifying their Facebook and Twitter followers. This feature can be managed on the settings page.
On the main Pinterest page, a “pin feed” appears, displaying the chronological activity from the Pinterest boards that a user follows.
A “board” is where the user’s pins are located. Users can have several boards for various items such as quotes, travel or, most popularly, weddings. A “pin” is an image that has either been uploaded or linked from a website. Once users create boards and add pins, other users can now repin , meaning they can pin one user’s image to their board as well. Once the user has set up their account and boards, they can browse, comment, and like other pins . Users might be discouraged by repeated images and difficult-to-follow direct linking features. Pinterest has also added the option of making boards “secret” so that the user can pin to and view boards that only the user can see when logged into their own account.
Pinterest does not generate its own content; rather, it draws from many resources around the web and compiles them in one convenient location for users.
LESSON 8: Basic Web Page Creation
1.) What are the advantages and disadvantages of a WYSIWYG editor?
ADVANTAGE :
-You don’t need any scripting/coding experience.
– It’s simple and easy for beginners.
– Everything moves fluently, and you can easily preview what you want.
DISADVANTAGE :
-A lot of HTML code churned out by the editors is superfluous which makes the web pages bulky in file size
-WYSIWYG editors let you ignore certain aspects that are important.
-WYSIWYG editors simply do not provide enough support and help in optimizing your web site for search engines.
2.) List Down (3) more WYSIWYG web hosting services and their URL.
– Weebly Web Builder ( https://www.weebly.com/ )
– Wix Web Builder ( https://www.wix.com/ )
– Siteground Builder ( https://www.siteground.com /)
LESSON 9: Collaborative ICT Development
Lesson 10: interactive multimedia.
World Wide Web
world-wide-wait
videos (youtube)
sound, music, or audio (soundcloud)
online games (farmville)
online tests (iq and personality test)
courseware (e-learning courses)
podcasts (ted talks, ear biscuits, the starters, stuff you should know)
vodcasts (video game high school and gmm)
LESSON 11: ICT as Platform for Change
The Role of ICT in Recent History
Throughout recent history, the Philippines have been one of a few nations that demonstrate unity for a call to action or social change. These campaigns for social change would have not been successful if it were not for ICT.
- EDSA (PEOPLE POWER REVOLUTION). The people power revolution lasted from 1083 to 1986. During a radio broadcast of Radio Veritas, Cardinal Sin encouraged the Filipinos to help end the regime of then President Ferdinand Marcos. A major protest took place along the EDSA from February 22 to 25, 1986 involving two million Filipinos from different sectors. These included civilians, political parties, the military and religious groups.
- EDSA DOS. This is also known as the 2001 EDSA Revolution, happened during January 17 to 21, 2001. It was fueled after 11 prosecutors of the President Joseph Estrada walked out of the impeachment trial. As a result, the crowd in EDSA grew over the course of a few days through text brigades.
- Million People March. This is a series pf protest that mainly took place in Luneta Park from august 22 to 26, 2013. There were also several demonstrations that happened around key cities in the Philippines and some location overseas. The organizers and promoters of the Million People March used Facebook and Change.org as their, mediums.
- Yolanda People Finder. Recent storms in Philippines history gave birth to the People finder database powered by Google. During typhoon Yolanda, the people finder was a vital tool for people across the globe to track the situation of their relatives. This proved to be successful and is now adapted by more organizations to help people track relatives during calamities.
Change.org is dubbed as the “world’s platform for change” where anyone from the online community can create a petition and ask others to sign in it. During the past times petitions are only done through signing a paper, usually done by a group asking for signatures via travel. Change.org gives access to more people by allowing the online community to affix their digital signatures on petition.
Signing an Online Petition
- Visit Change.org
- Change.org works this way. If this is your first time to use Change.org, click Sign up or log in with Facebook. Otherwise, just input your log in details.
- You can then start your own petition, but for now click on any petition you want under tending petitions.
- Read the petitions description to see if this petition matters to you. If it is, sign the petition by filling up the information on the right side of the screen.
- Share the petition on Facebook to promote it.
Alternatively, you can check out petitions of your friends on Facebook, and then click on those petitions to read about it and sign it.
LESSON 12: ICT Project for Social Change

Five elements of a concept paper
1 .Introduction -includes tour group’s mission and vision and a brief introduction of your project.
2. Purpose -includes the reasons why this project is worth your group and your sponsor’s time, effort and money.
3. Description -includes all the necessary information about the project. In ICT, it involves the sites you are going to produce and the purpose of each and how they work in unison.
4. Support -contains the budget needed for the project. Some concept papers do not specify any amount requested from the sponsor.
5. Contact information -includes information on how the group be contacted.
Simplified ICT Project Process Overview
1. Planning -Involves the following task (but not limited to):
- Conceptualizing your project project
- Researching on available data about your topic
- Setting deadlines and meetings
- Assigning people to various tasks
- Finding a web or blog host
- Creating a site map for tour website
- Listing down all applications, that you need including web apps
- Funding (If applicable)
2. Developmen t-involves the actual creation of the website(s), involves the production of images, infographics, etc.
3. Release and Promotion -involves the actual release of the website for public view and promoting it. Promotion typically starts before the actual release.
4. Maintenance -involves responding to feedback of your site visitors and continuing to improve your website.
LESSON 13: ICT Project Publication and Statistics
Monitoring Site Statistics on Different Platforms
Once you log in to your WordPress account, you are on the Reader tab by default. Simply click on My Sites and from there you will see the statistics for your blog.
In your Facebook page, a summary of the statistics will appear on the right side of your cover photo: Hovering your mouse pointer over “Post Reach” will give you more insights on which recent post reached the most people: Clicking on the Insights tab will give more in-depth statistics:
- Overview – contains the summary of statistics about your page
Definition of terms on your Facebook statistics:
Reach: Organic – your posts seen through the page’s wall, shares by users, and the news feed
Reach: Paid – your posts seen through paid ads
Post Clicks – number of clicks done to your posts
Likes, Comments, and Shares – actual interaction done by your audience either through liking the post, commenting on it, or sharing it on their walls.
- Likes – contains the statistics about the trend of page likes
- Reach – contains information about the number of people who was reached by your post
- Visits – contains data of the number of times your page tabs (like the Timeline) are visited
- Post – contains data showing when (day and time) you site visitors visit your site
- People – contains statistics about your audience’s demographics (age, location, gender, language, and country). It is also includes demographics about the people you have reached and engaged with.
Demographics refers to the statistics characterizing human population usually divided by age, gender, income, location, and language.
LESSON 14: ICT Project Maintenance
Creating online surveys feedbacks forms. The Internet will give you a lot of options in gathering your audience’s feedback. The only difference that you and your group may notice is how these services are presented. Some of them, because they are free to use, may have too many ads or some features are lacking. In any case, it’s your group’s choice which of these services is t cumbersome to reach your objective. Google offers one of the easiest ways to gather user’s feedback. Google forms allow your audience to answer a set of questions you have set. These can be used for surveys, feedback, online registrations, and customer care support.
4. You will be taken to Google Form’s interface: Next is ! Lets move on to ! 6. Once you are done editing the question, click Done. 7. To add a new question or item, click on Add Item, clicking on the drop down arrow at the right side of the Add Item button will bring up other options for layout: a. Section Header – adds a header for a specific a part of your survey. b. Page break- adds a page break which means that the items at the button of the page will be added to the next page: necessarily if your survey is too long. c. Image- adds an image to your survey d. Video- adds a video to your survey
iii. Multiple Choice – can be answered by only one answer in a set of options Creating feedback forms using Google forms Lesson objectives • Evaluate the effectiveness of their online campaign through user feedback; • Improve the online campaign using various tools; and • Check the impact of their online campaign.
1) Open your browser and go to drive.google.com 2) Sign in or create an account. 3) On the left hand hair of your My Drive page, click New> More> Google Forms
Steps ! 5. You may now fill out the form questions: A. Question Title- Includes the question that will be answered by your audience. B. Help Text- Creates a subtext under the question to give more information about a question. C. Question Type- changes the type question according to your preference. These questions include: i. Text – can be answered in a short text. ii. Paragraph Text – can be answered in a long text. iv. Checkboxes – a question that can be answered with multiple answers in a set of options. v. Choose from a list- similar to a multiple-choice question but options are revealed in a drop-down list. vi. Scale- a question that can be answered with a numerical range. vii. Grid- a question that contains sub questions with similar options as shown; • Date- a question that can be answered with a specified date • Time- a question that can be answered with a specified time .
d. Advanced Settings: Contains more options for the specified question type. 8. Edit the Confirmation Page option at the bottom as you see fit. A. Show link to submit another response- allows the user to answer the same form again. B. Publish and show a public link to form results- allows users to see the summarized results for your survey. C. Allow responders to edits responses after submitting- allows users to back and edit their answers .
9. Click the Send Form button. The Send Form dialog box will appear these options as you see fit.
a. Link to share- contains the URL that you can share on your website. b. Embed- contains an embed code to attach to your HTML. c. Short URL- generates a shorter URL necessary for limited spaces like sharing on twitter. d. Share link via- allows you to share the link to Google+, Facebook, and Twitter. e. Send form via email- allows you to share the form via email. f. Add collaborators- Allows others to edit your form, necessary when working on groups.
1. The easiest way to view the result is viewing a summary of the responses. Click on Responses> Summary of Responses. 2. You will be taken to a Summary of Responses page. This is particularly useful for viewing your results from time to time.
However, after a set amount of time, you may want to use this data in a spreadsheet and eventually create your own charts. 3. To use the data collected through responses, click View Responses button found on the upper part of the page.
Analyzing your Google Forms Result 4. Choose if you want to create a new Google Sheet as the destination of your response results or if you want to put it on an existing Google Sheet.
LESSON 15: Disadvantages of ICT
Cybercrimes are illegal acts done through the use of the internet. People all over the world use the Internet to commit a host of crimes, some of which the public doesn’t even know are capable of being done electronically.
1 . Phishing and Spoofing

2. Blackmail/Extortion

Extortion (also called blackmail , shakedown, out wresting, and exaction) is a criminal offence of unlawfully obtaining money, property, or services from a person, entity, or institution, through coercion. Refraining from doing harm is sometimes euphemistically called protection. Using the Internet to threaten to cause damage with the intent to extort from any person any money or other thing of value.
3. Accessing Stored Communications

4. Sports Betting

5. Non-Delivery of Merchandise

6. Electronic/ Cyber Harassment

7. Child Pornography

8. Prostitution

Persuading, inducing, enticing, or coercing any individual to travel in interstate commerce to engage in prostitution.The internet has become one of the preferred methods of communication for prostitution, as clients and prostitutes are less vulnerable to arrest or assault and for its convenience
9. Drug Trafficking

Delivering, distributing, or dispensing a controlled substance by means of the Internet. Darknet markets are used to buy and sell recreational drugs online. Some drug traffickers use encrypted messaging tools to communicate with drug mules. The dark web site Silk Road was a major online marketplace for drugs before it was shut down by law enforcement (then reopened under new management, and then shut down by law enforcement again)
10. Criminal Copyright Infringement

Share this:
Published by Joyce
A college student. Made this page for my final exam for ICT back when I was SHS. View all posts by Joyce
28 thoughts on “Empowerment Technologies LESSONS 1-15”
Thank you po! maam and sir for sharing us
Good Day, this is a very good module, can I use this module as my reference? Thank you.
Absolutely comprehensive! Thank you!
thank you for sharing this online. New teacher here. not my piece of pie but it was assigned to me this school year. can i use this for my class? thank you in advance.
I have learned a lot in this lesson. This lesson helped me understand more about this subject.
No coomment
Will it’s okey
- Pingback: CENTENO’S EMTECH BLOG – Site Title
I learned a lot because of this lessons.
There are a lot of crimes in social media that we need to careful our social media accounts.
From grade 12 Loreal
Baliwagan,Balamban,Cebu
how can i get a copy
AMAZING PLEASE SEND ME A COPY OF THIS.. THANK YOU
- Pingback: E-LEARNING OF EMPOWERMENT TECHNOLOGY – My website
thank you for your blog, can I use this for one of my references. very informative
Thanks Very Much!!! God Bless
Thank you for this may I ask a soft copy of the presentation for this? here is my email [email protected] thank you so much
- Pingback: Top 10 công nghệ 11 bài 1 mới nhất năm 2022 - Tốp 10 Dẫn Đầu Bảng Xếp Hạng Tổng Hợp Leading10
I was tasked to teach this subject. It’s my first time to teach empowerment technology. Please if allowed can i use your lesson made for my subject. Thanks a lot. Your ready made lesson really helps me a lot. God bless sir
maraming salamat! may lesson 16 up pa po ba??
This design is spectacular! You certainly know how to keep a reader amused. Between your wit and your videos, I was almost moved to start my own blog (well, almost…HaHa!) Excellent job. I really loved what you had to say, and more than that, how you presented it. Too cool!
Incredible points. Solid arguments. Keep up the great effort.
Also visit my site :: เครดิต ฟรี 50 bone168s
So nice and thank you
Reblogged this on Polong NHS Senior High School .
- Pingback: Empowerment Technologies LESSONS 1-15 – Study Routines
Leave a comment Cancel reply

- Copy shortlink
- Report this content
- Manage subscriptions

IMAGES
COMMENTS
Quiz number 1- empowerment technologies essay. Course: Bachelor of Science in Business Administration (BSBA) ... Answer the foll owing questions. 1. ... in technology and co mmunication tha t can think o f. Before the 21st century, mobi le phones exi sted.
Empowerment technology isn't just about providing new ways to communicate or collaborate; it's also about breaking down barriers and creating an inclusive environment where everyone can thrive. By leveraging the power of these technologies, you can help promote a more inclusive society where diversity is celebrated and valued.
What is Empowerment Technology? Empowerment Technology is a subject that focuses on harnessing the power of technology to enhance our lives, communicate effectively, and make informed decisions in the digital age. In this course, we'll explore how technology can be a tool for personal, social, and professional empowerment. Course Objectives:
empowerment technology. strategy that aims to give individuals the tools and resources necessary to take initiative, as well as gather and analyze information or situations, thus making informed decisions to solve problems and improve services or performance." empowerment. - Empowerment requires being information literate and technology literate.
Background Information and communications technologies (ICTs) have empowered people to communicate and network at a global scale. However, there is lack of in-depth understanding of the use of ICTs for women's empowerment. This study examines how the concept empowerment is defined, utilized and measured in research studies, the existing evidence on the use of ICTs for women's empowerment and ...
Essay in Empowerment Technologies. It is an essay on our subject in Empowerment Technologies to pass the... View more. Course. Mathematics (Math 101) 267 Documents. Students shared 267 documents in this course. University Technological University of the Philippines. Academic year: 2014/2015. Uploaded by: Samantha Cruz.
Empowerment Technologies or E-Tech is a hard and difficult subject for me. One thing's for sure is that, I, myself, didn't know fully about the subject. It is hard because some of our lessons are difficult for me to understand and I'm not good in technology-related stuff. However, there are times that I can understand what our teacher is ...
Empowerment technology is a powerful tool that can be used to promote social, economic, and political empowerment, especially for women. By providing individuals with access to information, resources, and training, it can help to break down barriers and create opportunities for those who have been marginalized or excluded from mainstream ...
LESSON 1: INTRODUCTION TO ICT. ICT - Information and Communication-. It deals with the use of different communication technologies such as mobile phones, telephone, Internet to locate, save, send and edit information. Is a study of computers as data processing tools. It introduces students to the fundamental of using computer systems in an ...
Test your knowledge of information and communication technology (ICT) with this quiz on Empowerment Technology Chapter 1. Explore topics such as ICT applications, research, productivity, safety, and ethics. Compare and contrast different online platforms, sites, and content to effectively achieve class objectives and address challenges. Identify the essentials of ICT and its importance in ...
Partial preview of the text. Download Empowerment Technologies Reflection Paper and more Computer science Essays (high school) in PDF only on Docsity! Claire Gabrielle S. Martin Empowerment Technologies 12-ABM A Ms. Madilaine Claire D. Basco +++Applied 121d was a subject code we were not familiar with even if we are met almost all of our ...
Developing a Filipino Psychology. Copy of filipino psychology-pepua-marcelino. The 1872 Cavite Mutiny. Activity-on-Global-Culture-and-Media Psychology hence the century. EMPOWERMENT TECHNOLOGY SUMMATIVE TEST QUARTER 1 MODULE 1-2 republic of the philippines department of education region calabarzon division of san pablo crecencia.
Which is the best example of current technology that demonstrate full Web 3.0 technology, A. E-commerce sites like Lazada or Shopee., B. Self-correcting spelling functions in Microsoft application., C. Smart phone applications., D. Web 3.0 is not yet fully realized or developed., , Short wave radios during World War II were big and bulky but ...
This is the empowerment technology exam. Subject. Education. 999+ Documents. Students shared 1218 documents in this course. School Balingasa High School. Academic year: 2022/2023. Uploaded by: GR. GERALDINE ROSA. Balingasa High School. 0 followers. 0 Uploads. 0 upvotes. Follow. Recommended for you. 31. Science 8 q1 mod5 colors-of-light Final ...